If you are running Linux on a PC, notebook or netbook with a Wi-Fi card it's "relatively" easy to use the system together with Wireshark for WLAN tracing. Since Wireshark version 0.99.5, even WPA decryption is supported so Wireshark also decodes the packets from other devices in your network.
Relative is a relative term though as it seems that depending on the Wi-Fi hardware and the drivers used, there are different ways to set the network card and protocol stack into monitoring mode. This is necessary to send the full 802.11 Wi-Fi frames to Wireshark. On the Asus eeePC 701 running Xandros Linux it works as described in this post.
On my new Acer Aspire One D250 with an Atheros AR242x 802.11abg wireless chip running Ubuntu 9.04, things work a bit differently and it took some experimenting to figure things out:
The first step to install "iw" via the Synaptic package manager. Once installed, setting the Wi-Fi card into monitoring mode is quite straight forward with a couple of commands via a shell:
sudo ifconfig wlan0 down
sudo iw dev wlan0 interface add mon0 type monitor
sudo ifconfig mon0 up
At this point the Wi-Fi card stops working as a normal network interface and Wireshark gets a new network adapter "mon0" that can be used for tracing in promiscuous mode. Unlike with the original eeePC that required the Wi-Fi card to be configured for an unencrypted network before switching to monitor mode to prevent decryption of some packets before they reach Wireshark, this is not necessary on the Acer.
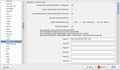 The picture on the left shows how Wireshark needs to be configured via the preferences menu for decoding encrypted packets. Different network cards might need different settings here. Changing the configuration and clicking on "apply" makes Wireshark go through all packets already traced and apply the changes. This way it's not necessary to generate a new trace which testing different settings. For the WPA decoding to work, it's necessary to know the encryption key to capture the key exchange of the device to monitor. In other words, the Wireshark trace has to be started and only then should the device to be monitored enter the network.
The picture on the left shows how Wireshark needs to be configured via the preferences menu for decoding encrypted packets. Different network cards might need different settings here. Changing the configuration and clicking on "apply" makes Wireshark go through all packets already traced and apply the changes. This way it's not necessary to generate a new trace which testing different settings. For the WPA decoding to work, it's necessary to know the encryption key to capture the key exchange of the device to monitor. In other words, the Wireshark trace has to be started and only then should the device to be monitored enter the network.
Once done with tracing the network adapter can be set back to normal operation with the following commands:
sudo ifconfig mon0 down
sudo ifconfig wlan0 up
Happy tracing!