Another year is drawing to a close and as in the years before I wondered what has happened during the year. And as always I was quite surprised when I went through my blog entries of the past 12 months about the amount. So here are my personal technology highlights of 2014:
LTE and Affordable Worldwide Internet access
Last year was the year when roaming in Europe finally became affordable. But that was nothing compared to what has happened in 2014. In July, I switched to a mobile contract that removed roaming charges for voice, data and SMS in Europe for 5 Euros extra a month. In addition, many network operators have now started to roll out LTE roaming and I had my first European and intercontinental LTE roaming experiences. And on top of that, my network operator of choice decided to apply the former EU data roaming rates to the rest of the world, thus enabling truly affordable global Internet access roaming. I've used it in China and the US during the year and it worked perfectly. On the technology side, I've also mused about data roaming costs from a technical point of view.
3rd Edition of my Book on Mobile Networks Gets Published
About 10 years ago the first edition of my book on mobile networks got published. Needless to say that over the years many things have changed and new technologies have appeared on the scene. I thus always kept updating the manuscript and 2014 saw the publication of the 3rd edition of 'From GSM to LTE-Advanced – An Introduction to Mobile Networks and Mobile Broadband'.
Network Function Virtualization
In the making for a number of years now, the standardization and discussion around Network Function Virtualization is taking on shape. Having used virtualization on the desktop for quite some time now to do things like locking up Windows in a virtual machine I decided it was time to write an NFV primer. You can find the result here.
CyanogenMod, Root Access and 'Smartphones are PCs now'
Last year came the end of Symbian for me and I've been struggling since then to get my privacy back, i.e. to make Android stop talking to Google and others all the time. A fist step to this goal was to switch to CyanogenMod which brought some disadvantages but opened up a whole new world for me. With CyanogenMod and root access, smartphones really started to feel like computers to me new and I wrote a long blog entry about the next revolution in computing based on those experiences. From a practical point of view I figured out how to stop my smartphone and other devices from contacting Google and advertisers all the time to regain my privacy and to bring pleasure back to web surfing on mobile. In September I automated the blocking list update process and put the details on Github so others could benefit as well.
Security and Privacy
Like last year, security and privacy have remained important topics for me, as Edward Snowden's revelations on the scope and depth of mass surveillance continues to baffle me. 'Raising The Shields' has been my motto since and I've put together a number of things to encrypt as much of my communication as possible. With a Raspberry Pi I've put together a security gateway for VNC remote screen sessions and to encrypt both legs of the connection by using SSH tunnels. Another Raspberry Pi and a Banana Pi for performance reasons have since been put into use as OpenVPN servers. And to encrypt all my Internet traffic when I'm in public places such as hotels, I've put together scripts and configuration files to configure a Raspberry Pi as an OpenVPN client and Wi-Fi access point. The scripts and configuration files are on Github for those of you with similar needs.
2014 has also been the year of massive security issues. Heartbleed is the one that will probably be remembered best and I had a posts about whether my Raspberry servers were vulnerable and the extend of just how bad this discovery was and wondered why nobody discussed the NSA's denial that it didn't know about this and what this would mean if it was actually true.
Over summer break, I decided to have a closer look at how assisted GPS works and found out that SUPL, one of the protocols used by some mobile chipsets reaveals my identity and location to Google every time I fire up the GPS chip. For those of you who care about the details I had a blog posts with further technical details here and how to trace a SUPL request here. But even if assisted GPS is switched off, it's still not easy to hide your location, even if a VPN is used as described here.
I was probably not the only one who was shocked to hear that whoever was behind Truecrypt decided to abandon the project as I've been using the software on many devices. Some projects followed to review the source code and to see if someone else could continue to maintain it. I'm not sure how that turned out because I decided to switch to dm-crypt (details here and here) which is truly open source and, from what I can tell, peer reviewed.
Owncloud and How to Enable Everyone
Last year I started to use Owncloud to host my own 'cloud services' at home and this has given rise to a number of interesting thoughts and projects. In 2014, I migrated my Owncloud installation to a NUC for higher performance. One problem with Owncloud is that it requires quite a bit of technical knowledge to get going. In other words, it's something for the nerds as setting up Dynamic DNS, configuring port forwarding, getting an SSL certificate and struggling with Internet lines at home without public IP addresses is not everybody's cup of tea. So over the course of the year I put together the pieces of the puzzle and came up with an idea of how to 'home cloud enable' everyone to keep private data private.
Open Source – The Joy of Fixing It Yourself
2014 was also the year I got rid of Windows at home. All computing devices in the household are running on a Linux distribution now and Windows is banned into Virtual Machines and as an alternate OS on a single machine for those very few occasions for which a Windows running on bare metal is required. Over the year I have booted to Windows at home perhaps twice.
Open source is great because you can fix things yourself. To that end I've reported a number of Owncloud issues on their Github presence, I supplied code to extend the Selfoss RSS Server/Reader platform with new functionality I wanted to have and I set up two projects on my own on Github (The VPN Wi-Fi Access Point and the stuff required for privacy on CyanogenMod described above).
And finally on the programming side, open source has helped me a lot to better understand the fabrics of the web. As part of this I worked through a book about PHP and mySQL as sometimes books still trump online research and implemented a private database application with a web frontend. As this was so much fun I used my new knowledge to put together an automated system for testing the reliability of the Wi-Fi and cellular connectivity of mobile devices with a web based interface.
Fiber Connectivity
A 25 Mbit/s downlink and 5 Mbit/s uplink at home is not bad but once you've seen what a Fiber To The Home (FTTH) connection can do it seems to be slow indeed. When I benchmarked that 1 Gbit/s FTTH connection in Paris I got a sustained 260 Mbit/s in the downlink direction. Technical details and images of the installation can be found here. But while this is all nice, I wonder if fiber will become the new monopoly and if perhaps G.fast will be a remedy!? Time will tell.
From the Terabyte SSD to Vintage Computing
That 500 GB SSD I bought last year is still brand new but I managed to use all it's capacity only a year later. So I had to upgrade my notebook once again and have ended up with a 1 TB SSD. Again, I used the disruptive occasion to get rid of a couple of other limitations by creating a separate OS partition from a dm-crypted data partition which allows me to backup and restore the OS partition in a few minutes compared to the several hours required before.
Going back in time was equally exciting. At the beginning of the year I was in Silicon Valley and had some time at last to go to the Computer History Museum. Later in the year I also visited to the Heinz Nixdorf museum in Paderborn, Germany, which declares itself as the biggest computer museum in the world. And indeed, it is a museum not to be missed if one has an interest in vintage computing.
And last but not least: This year was the 10th anniversary of my first 3G mobile. It's been only 10 years but the mobile landscape has changed dramatically during this time.
I can hardly believe all of this happened in 2014. After all, the year felt so short…
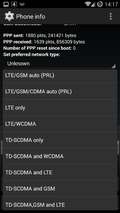 These days I often wished I could disable GSM in my phone and live with the occasional coverage hole rather than falling back to GSM for a while. I acutally have quite a number of reasons for that:
These days I often wished I could disable GSM in my phone and live with the occasional coverage hole rather than falling back to GSM for a while. I acutally have quite a number of reasons for that: