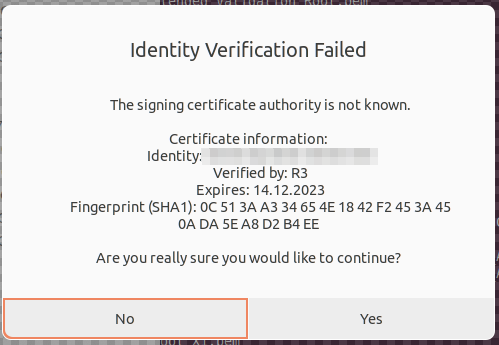
After upgrading my notebook to Ubuntu 22.04, one of the few quirks that I had to deal with was that the file manager suddenly threw a security warning when I wanted to mount my Nextcloud DAVS share that is protected with a Letsencrypt certificate. Very strange, as this worked flawlessly in Ubuntu 20.04. It doesn’t break the functionality, but getting a certificate warning each time I mount the network drive is not acceptable. It turns out that for whatever reason, Ubuntu 22.04 doesn’t have the Letsencrypt chain of trust in their certificate store. Web browsers like Firefox don’t have the issue on 22.04, as they come with their own certificate store. For some strange reason, there isn’t really a description of the problem on the net, or it’s well hidden by other search results, so it took me a while to figure out how to import Letsencrypt’s current certificate chain. But I finally figured it out and here is how it is done:
The first thing to do is to see if the required certificates are in Ubuntu’s cert list:
trust list | grep -C 2 "R3"
This should result in:
$ trust list | grep -C 2 "R3"
pkcs11:id=%C1%F1%26%BA%A0%2D%AE%85%81%CF%D3%F1%2A%12%BD%B8%0A%67%FD%BC;type=cert
type: certificate
label: GTS Root R3
trust: anchor
category: authority
--
pkcs11:id=%14%2E%B3%17%B7%58%56%CB%AE%50%09%40%E6%1F%AF%9D%8B%14%C2%C6;type=cert
type: certificate
label: R3
trust: anchor
category: authority
If only the ‘GTS Root R3’ is listed, you are missing the ‘R3’ cert used by Letsencrypt. If missing, get the certificate from their servers:
wget https://letsencrypt.org/certs/lets-encrypt-r3.pem
Once downloaded, change to root, copy the file into the user certificate path, rename it and make it known to the system:
# Copy PEM files to /usr/local/share/ca-certificates # Create the /usr/local/share/ca-certificates directory if not yet present. # sudo -s cd /usr/local/share/ca-certificates/ cp /home/xxx/yyy/zzz/*.pem . # Change the file name suffix to “*.crt”. # mv lets-encrypt-r3.pem lets-encrypt-r3.crt # Integrate the cert into the system's certificate set # sudo update-ca-certificates
Once done, the error message goes away. That is, of course, until the cert expires, which will be in September 2025.
Thanks to Gerrit and the staff at the university of applied sciences Schmalkalden for posting parts of the solution.
Rather than adding it to one’s root certificates trust store I’d advocate for server operators to include the missing cert as a chain cert on the server. This is also what commonly used tools like certbot, getssl etc. do.
In other words, your Nextcloud DAVS simply lacked the configuration to include the R3 chain certificate.