When traveling, I often use VPN tunnels to secure my data transfers e.g. in open Wi-Fi hotspots or to prevent cellular network based transparent "optimization" algorithms from compressing webpages and pictures. There are a number of companies out there that offer gateways around the world and good OpenVPN support. However, one thing I can't do with them is to securely access my resources at home (e.g. my NAS). Also some countries I travel to block access to their public gateways. For both reasons, I long wanted to set up my own OpenVPN Gateway at home. Finally, I had some time to my surprise the necessary hardware, a Linksys WRT-54GL can be had for 38 Euros. An OpenVPN gateway at home for 38 Euros, I call that a good price.
It was a bit tricky to get the gateway up and running though, I spent the better part of three evenings to get things working. Let's count it as part of the adventure. 99% of how to get the gateway up and running can be found in this post on How-To-Geek. One of the best tutorials on how to set-up something complex I have ever seen. Highly recommended. In short it works as follows:
- Get a Linksys WRT54GL router or any other router on which the open source DD-WRT Linux can be installed.
- Install the OpenWRT client, preferably on a Windows machine as the tutorial linked above shows how to do it on this OS, and use the tools that come with the software to generate a number of keys and certificates needed for the OpenVPN server and client. This is the tricky part but the tutorial describes it in detail.
- Copy/paste the required certificates to the OpenVPN router. One point that's not contained in the tutorial is that some of the key and certificate files created contain some explanatory text that must not be copied/pasted into the OpenVPN configuration. If done, the configuration won't be saved in the router.
- Make the OpenVPN server thread start automatically. As I use my DSL router as a gateway to the Internet, a number of configuration steps are required that are not described in the tutorial. As the VPN tunnel uses its own IP address subnet, it is necessary to create a static route to this subnet in the DSL router's IP configuration. Also, the NAT firewall has to be configured to forward UDP port 1194 to the VPN gateway router (I decided not to use TCP as described in the tutorial). And finally, for some strange reason, the OpenVPN server thread does not start automatically in my setup, probably because I don't use the WRR54GL box as an IP gateway with NATing. This can be fixed by adding the following command to the startup commands in the router GUI:
openvpn –config /tmp/openvpn/openvpn.conf –route-up /tmp/openvpn/route-up.sh –down /tmp/openvpn/route-down.sh –daemon
- Disabling Wi-Fi: As I only want to use the router as a gateway there is no need for the Wi-Fi access point running. Unfortunately, there is no GUI option to disable Wi-Fi and I couldn't come up with a clean solution for it. There is a command to disable the Wi-Fi. However, if executed as a startup command the router ends up in a reboot loop. The kludge that works for me is to run the disable Wi-Fi command as a cron job periodically. Here's the line for the cron job:
*/5 * * * * root wl radio off
- Partial or Full VPN: The VPN tunnel can be used for tunneling only the traffic for the home network or as a full IP tunnel depending on how the client is configured. In full tunnel mode (the tunnel is used as a gateway to the Internet) all traffic is sent over the tunnel into my home network and from there to the Internet. When using the tunnel to encrypt all traffic one additional manual setting required in the client is the DNS server as it's not configured when the tunnel is established. An easy solution is to use Google's DNS server IP address (8.8.8.8).
- Windows Clients: I got the setup working just fine with Ubuntu 12.04 as a client machine. I also tried Windows 7 and Windows XP but couldn't get the tunnel working. It establishes just fine but no data is flowing through it, not even to server side IP address. Very strange as the tutorial was written for Windows 7. But it's not my primary platform anyway so I grinded my teeth and ignored it for the time being.
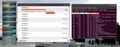 Performance wise, the 200 MHz ARM processor in the router has its limits. The processor maxes out at a throughput of around 4.5 MBit/s as shown in the picture above. At this speed, the OpenVPN server thread takes 98% of the CPU time. My current VDSL uplink speed is 5 MBit/s so I am close to the limit. More up to date and more expensive routers that can run DD-WRT will probably do even better as they have much more capable ARM processors and clock rates of 600 MHz and beyond. As not the downlink speed of the DSL or cable connection is the limit but uplink line rate, which is usually much slower, the old low cost WRT54GL router will do just fine for most people.
Performance wise, the 200 MHz ARM processor in the router has its limits. The processor maxes out at a throughput of around 4.5 MBit/s as shown in the picture above. At this speed, the OpenVPN server thread takes 98% of the CPU time. My current VDSL uplink speed is 5 MBit/s so I am close to the limit. More up to date and more expensive routers that can run DD-WRT will probably do even better as they have much more capable ARM processors and clock rates of 600 MHz and beyond. As not the downlink speed of the DSL or cable connection is the limit but uplink line rate, which is usually much slower, the old low cost WRT54GL router will do just fine for most people.
There we go, infinite possibilities opening up with my new VPN gateway and I learned a lot in the process of making it work.
Thanks for the useful article showing how much fun can be had with a cheap router, some alternative firmware and a bit of time an persistence to work out how to set things up 😉
You may be interested in the Android app “OpenVPN for Android”, which I discovered recently. It runs without root, imports OpenVPN confg files (get a working setup on a PC first and then just import it) and has been working flawlessly for me for the last few weeks. Top notch!