When it comes to roaming in Europe as an EU citizen, there is one sore spot on the continent: Switzerland. As the country is not part of the union, EU roaming does not apply to it and it depends on your prepaid or postpaid contract if voice and data roaming while being in Switzerland is included. While my German network operator of choice has always included Switzerland in EU roaming, a lot of other German network operators and MVNOs have not. Also, the French network operator of choice of a member of our household did not have it in the contract for many years, either. But fortunately, things have changed quite a bit this year.
Continue reading The Switzerland Roaming Problem (Almost) SolvedCategory: Uncategorized
Fantasizing AI – Caddy Reverse Proxy and Basic Authentication
Recently, I wanted to replace my somewhat outdated reverse proxy setup in the virtual machine I run a lot of docker based services in for a much simpler Caddy setup. One docker-compose.yml file with a few lines is all it takes. I was pretty sure this wouldn’t take too much time, because I thoroughly tested Caddy on two other VMs which I used to run internal services. And indeed, everything worked fine until I came to the point where I needed to configure basic HTTP authentication for two of my services. Unfortunately, Caddy stubbornly ignored the second username/password combination I configured. I did test HTTP basic authentication, but only with one username/password combination. It looks like you can never test enough. Darn!
After almost two hours and only getting delirious suggestions from a number of different AI search engines, I aborted the approach and rolled back the virtual machine to the old reverse proxy configuration. It’s always good to have a quick fallback when things come apart and this worked well. Still, I felt defeated but didn’t have the time to investigate further. So I postponed the activity until after Christmas.
Continue reading Fantasizing AI – Caddy Reverse Proxy and Basic AuthenticationRaising the Shields – 12 Years Later – Part 4 – How To Back It All Up?
OK, one more topic is still missing in my story about running my own cloud: How do I back it all up? Before answering the question, it is of course important to define which scenarios to protect against with backups. And, not surprisingly, I have made good use of my backups over the years to restore accidentally or unintentionally deleted data. Read on for the details.
Continue reading Raising the Shields – 12 Years Later – Part 4 – How To Back It All Up?Raising the Shields – 12 Years Later – Part 3 – Maintenance
So yes, I have quite a bit of physical infrastructure in various places and quite a lot of services running on them. So how can all of this be maintained with as little effort as possible? After all, doing software upgrades is not an exciting or entertaining task, so the process has to be automated as much as possible without loosing visibility if updates have gone smoothly or not.
While a decade ago, I only had a single Raspberry Pi in place, an apt update && apt upgrade did a good job. But with around 20 virtual machines these days and about the same amount of containers running on 4 distributed servers, this is no longer a viable approach.
Continue reading Raising the Shields – 12 Years Later – Part 3 – MaintenanceThings That Moved Me in 2025
It’s the time of the year again to spend a few minutes looking back to the major things in tech that happened for me this year and ended up on this blog. So without further ado, let’s jump right in and have a look at the things that moved me in 2025.
Continue reading Things That Moved Me in 2025Raising the Shields – 12 Years Later – Part 2 – Hardware
In the first part of this series, I’ve given you an overview of the services I host on my own servers to be independent of hyperscalers and to keep my data private. The number of services is stunning so there must be a lot of hardware standing around. Well, not quite so, let’s have a look:
Continue reading Raising the Shields – 12 Years Later – Part 2 – HardwareRaising the Shields – 12 Years Later – Part 1 – Software
Back in 2013, i.e. 12 years ago, I decided that my private data must remain my own and started to self-host all essential services at my home. Not only for me, but also for my family and for my friends. Over those years, I’ve added more and more services and improved the redundancy of my setup. Some things came, some things went, and I thought it’s time to document my current hardware and software setup. So here we go with the software:
Continue reading Raising the Shields – 12 Years Later – Part 1 – SoftwareMore on SSD Wear: My Other Servers
In the previous post, I discussed how much data was written and read to and from the SSDs in my bare metal server in a data center over the course of a year. While this is my main server, I do have additional smaller servers at home for other purposes. One serves as redundancy for some of my services so that in case that server in the data center fails, I can recover from it quickly by temporarily switching over to the backup server. In these servers I have SSDs that are 6 and 8 years old, so they’ve been around for a while.
Continue reading More on SSD Wear: My Other ServersSSD Wear On My Server: 43 TB per Year
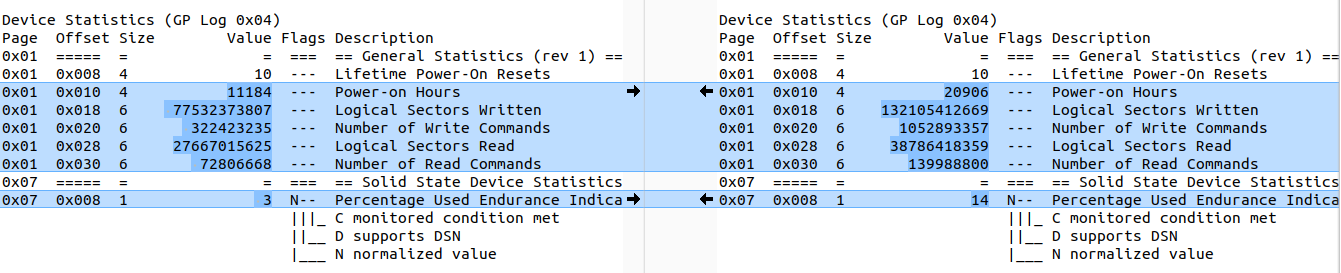
About a year ago, I moved one of my main bare metal servers from a datacenter in Finland to a datacenter of another provider in France. Like the old server, the current server has two 1 TB SSDs. Now that a year has passed, I was wondering how much data has been written to the SSDs by the applications running on it. While the number itself is interesting, the second interesting thing is how much life the SSD has left if my usage pattern remained the same. So let’s have a closer look.
Continue reading SSD Wear On My Server: 43 TB per YearNetwork Coverage Maps for All German Network Operators
I recently wanted to check where and how much LTE and 5G network coverage one of the German network operators really has these days. The problem: I couldn’t find coverage maps provided by that network operator on the Internet. But what I found instead was the maps of the Bundesnetzagentur, the German telecoms regulator, that show the fixed and mobile network availability of all German network operators. I had no idea that this website existed and I was positively surprised of how detailed the information is that is provided. So if you want to compare or just find out which network is available in a certain town, street or location, have a look there instead of trying to find coverage maps on the web sites of individual companies. Very nice! If you are aware of such coverage maps of network operators / regulators in other countries, please consider leaving a comment. Thanks!