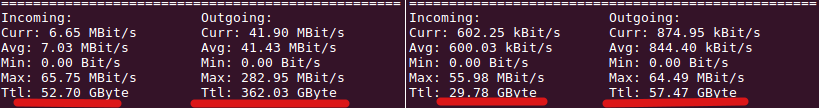
 An interesting piece of data when operating a video conferencing server is how much data is transferred over the course of a week or a month. When I initially calculated the potential amount of data my BigBlueButton server could potentially consume over the course of a month with 70 people in 4 sessions all showing their videos, 10 hours a day, 5 days a week, I came up with around 25 TB per month. That would have been all right since my virtual server rental contains 20 TB of traffic a month, and each additional TB is billed at a euro or two. But that was the theory, how about practice?
An interesting piece of data when operating a video conferencing server is how much data is transferred over the course of a week or a month. When I initially calculated the potential amount of data my BigBlueButton server could potentially consume over the course of a month with 70 people in 4 sessions all showing their videos, 10 hours a day, 5 days a week, I came up with around 25 TB per month. That would have been all right since my virtual server rental contains 20 TB of traffic a month, and each additional TB is billed at a euro or two. But that was the theory, how about practice?
Wi-Fi 6 – 802.11ax – Some Tech Resources
In 2019 and 2020, I’ve seen first Wi-Fi 6 (802.11ax) capable devices coming to the market, mostly smartphones. On notebooks, the standard still hasn’t made a real impact, even the current Lenovo Thinkpad X390 still comes with a Wi-Fi 5 (802.11ac) modem. Also, on the Access Point side, first products have become available but the impact so far is still small. Nevertheless, now is the time to have a look at the spec and here are a number of resources that give a good technical overview of what’s new:
BigBlueButton – Some Shortcommings
O.k., you must have figured it out by now, I’m a huge BigBlueButton fan. So while that is certainly true, there are a number of things I have noticed over the past few weeks that are not so nice (yet) and actually get in the way of getting some things done in an efficient way.
Base Station Changes Over The Years
 I have a cell site sitting on the building right across the street and two years ago I had a post here with some pictures of how the site has changed over the past 10 years. On average, changes are done every two years. So I guess it was time again when things were once again changed recently.
I have a cell site sitting on the building right across the street and two years ago I had a post here with some pictures of how the site has changed over the past 10 years. On average, changes are done every two years. So I guess it was time again when things were once again changed recently.
If you compare the picture above with those in my post 2 years ago, you will notice the additional small antennas that have been installed next to the bigger ones. Those are typical 5G n78 (3.5 GHz) active antenna systems (AAS)! In other words, the cell site has been upgraded to 5G!
802.11ac – 160 MHz Is Coming To My Home – At Least In Theory
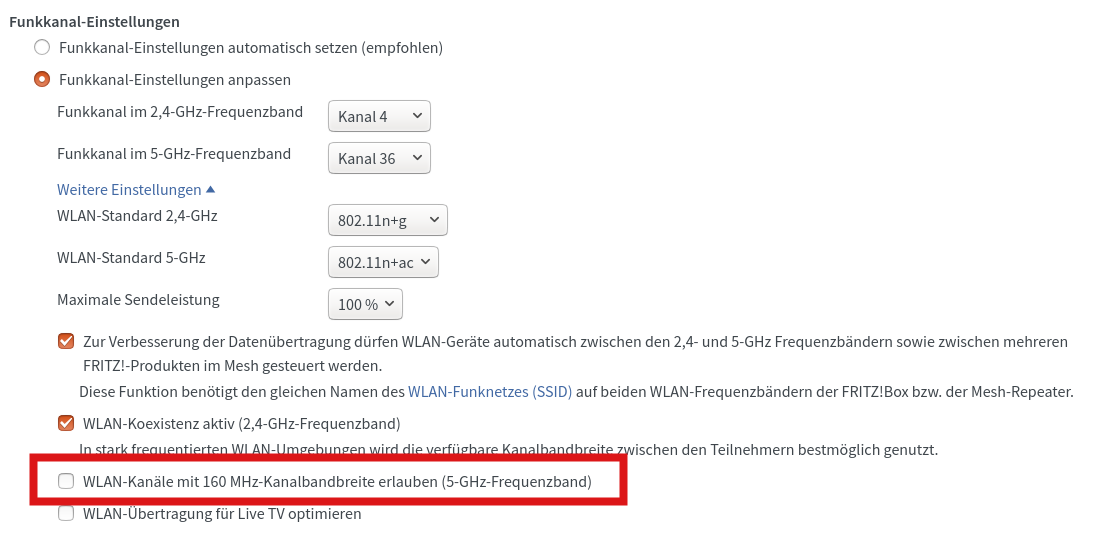 About two years ago I bought my current VDSL + Wifi Access Point router, a Fritzbox 7590. It is still AVM’s flagship model to this date with 802.11ac Wifi-5 support and it is good to see that the manufacturer continues to develop the software to this day. Especially the Wifi functionality around Mesh and 5 GHz operation keeps getting better and better.
About two years ago I bought my current VDSL + Wifi Access Point router, a Fritzbox 7590. It is still AVM’s flagship model to this date with 802.11ac Wifi-5 support and it is good to see that the manufacturer continues to develop the software to this day. Especially the Wifi functionality around Mesh and 5 GHz operation keeps getting better and better.
Continue reading 802.11ac – 160 MHz Is Coming To My Home – At Least In Theory
XMPP Voice and Video Calls with Conversations – A Dream Come True
 I’ve been waiting for this for 10 years! As I prefer to have as much of my private data flowing over the Internet in my own hands I’m running pretty much all of my ‘business critical’ web based services with open source software either at home or in a data center in Germany. The last piece of the puzzle that was missing was mobile and ‘casual’ end-to-end encrypted voice and video calling over my own infrastructure. I’ve had Nextcloud talk for a couple of years now and over the past two months have set up Jitsi and BBB instances for additional use cases. But all three solutions do not cover the ‘casual’ mobile calling experience where you just take your mobile phone and call someone else. Nextcloud, Jitsi and BBB would all have the potential to do that but non of them tried successfully covered this use case so far. But now Conversations, my mobile XMPP federated messenger app has made a quantum leap forward and has introduced voice and video calling!
I’ve been waiting for this for 10 years! As I prefer to have as much of my private data flowing over the Internet in my own hands I’m running pretty much all of my ‘business critical’ web based services with open source software either at home or in a data center in Germany. The last piece of the puzzle that was missing was mobile and ‘casual’ end-to-end encrypted voice and video calling over my own infrastructure. I’ve had Nextcloud talk for a couple of years now and over the past two months have set up Jitsi and BBB instances for additional use cases. But all three solutions do not cover the ‘casual’ mobile calling experience where you just take your mobile phone and call someone else. Nextcloud, Jitsi and BBB would all have the potential to do that but non of them tried successfully covered this use case so far. But now Conversations, my mobile XMPP federated messenger app has made a quantum leap forward and has introduced voice and video calling!
Continue reading XMPP Voice and Video Calls with Conversations – A Dream Come True
BigBlueButton – Moderator Only Video
Continuing my series on BigBlueButton server operation, I thought I spend a few words about how include those people in video calls that have old and not very powerful notebooks, smartphones or tablets. Most older devices still work ok in video conferences with 3 or 4 people. But in larger groups of 15-20 people, all showing their video feeds, less powerful devices start lagging behind and sooner or later quit entirely.
Android Data Backup: gvfs and rsync are Your Friends!
Most of you might know the feeling one has when that precious smartphone glides out of your hands, hits the street and goes straight to smartphone heaven: Horror followed by “damn, I haven’t copied my pictures yet”. The problem I had for many years is that backing up meant to know which pictures (or files in general) I had already copied and then only copying the new ones. That’s an exercise I didn’t even want to do once a month.
How nice would it be if it was just possible to rsync the phone to a backup drive. Turns out that this is actually possible!
Continue reading Android Data Backup: gvfs and rsync are Your Friends!
Client CPU and GPU Performance for Jitsi and BBB Videoconferencing
While I wouldn’t use Zoom for private video conferencing, I do use it for public conferences (on a burner notebook…) and noticed that their Linux client program is very resource optimized. Even when showing a dozen videos and piping the local video camera stream into the cloud, CPU processor load on my Thinkpad X230 notebook from 2013 is around 30-40% over all cores with Ubuntu 18.04. Compare to that to the 100% load across all CPUs when using Jitsi or BBB in Chromium when 8 videos are shown and one video stream sent to the centralized server. This made me wonder a bit if the load on newer notebooks is lower.
Continue reading Client CPU and GPU Performance for Jitsi and BBB Videoconferencing
LTE Event A6 for Carrier Aggregation
When LTE was launched a decade ago, setting up measurements was a simple thing. When a connection is established, the network typically instructs the mobile device to measure the signal strength of the currently serving cell and the signal strength of neighboring cells. The result is either reported periodically or when predefined events occur. When I last looked more closely, most networks were using event A1 for reporting when the serving cell becomes better than a threshold, A2 when the serving cell becomes worse than a threshold and A3 and A4 when a neighbor cell becomes better than the serving or than a threshold. That was nice and easy. And then over time things got way more complicated and I didn’t look more closely anymore. And yes, there is event B1 and B2 for inter-RAT measurements when things get bad and the network needs to consider GSM and UMTS neighbors.