In the previous entry on this topic I’ve given an overview of how to use a Linksys WRT54G Wireless LAN router OpenWRT, Kismet and Wireshark for Windows for wireless network monitoring and analysis purposes. This blog entry takes a look at the steps necessary to install the required software on the router.
The first step of the process is to buy a wifi router which supports OpenWRT, an alternative and free of charge Linux operating system for wifi routers. The routers supported by OpenWRT can be found here. I decided to buy a Linksys OpenWRT54GL as it offers enough RAM and Flash to run OpenWRT and has enough space for additional software to be installed later on. The price of the router was about 60 euros.
Installing OpenWRT
Once the router arrives, I suggest to use the built in software first to configure it as a Wireless Access point to verify the hardware works as expected. Once done, the router should be reset to run with the original out of the box settings. There are a number of different OpenWRT images depending on the router and router version. This page on the OpenWRT Wiki explains how to select the right image, from where to download it, and how to install it on the router. I chose to install this standard image for the Linksys WRT54G(L). In essence installing the OpenWRT firmware image is very simple by using the ‘update firmaware‘ functionality of the web interface of the original firmware. Be sure to read the installation page linked above for the fine print.
Installing a better Web Interface
After a router restart, open another browser window and access the router again. In a first step, select a new password. Afterwards, configure the router via the web interface so it is able to access the Internet. This is necessary as the software packages which are installed next are directly installed via shell commands on the router.
As the OpenWRT web interface is quite bare I suggest to install X-WRT next, a much improved web interface. This is done via a secure shell (SSH) session. This requires a Telnet/SSH program for Windows. I recommend using Putty.
Important note: Use SSH (port 22) to log into the router, telnet is not supported for security reasons. To log in use ‘root’ as user name and whatever password you’ve initially configured via the web access, even if that password is associated to a different user name.
Once you have shell access to the router, ensure the router can reach the internet by pinging a public IP address (e.g. ‘ping www.google.com‘).
Next, install X-WRT as follows: First ‘ipkg update” has to be typed in to load descriptions for additional software to the router. Once done, ‘ipkg install webif‘ installs X-WRT. Once the command has run successfully, the new web interface is available.
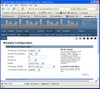
Before proceeding to the next main step one further thing should be done: On the web interface, select Wifi configuration and install the NAS package required for WPA/WPA2 encryption later on. This is done by pressing the corresponding button on the wifi configuration page. Once done, the wifi setup page looks like shown in the picture on the left at the beginning of this paragraph.
Installing Samba/CIFS package
The next major step is to install a driver on the router to be able to mount a Windows directory. This is needed as the Kismet dump files which contain the intercepted packets can get quite big and there is not enough space on the router to store them. This OpenWRT wiki entry describes the details. In short: ‘ipkg install kmod-cifs‘ downloads the driver. ‘insmod cifs‘ then install the driver into the Linux kernel. Both commands only have to run once as the driver insertion is permanent and survives reboots.
Once done, create a new directory on the router (e.g. ‘mkdir /martin‘) which will be used in a next step as a mount point. Afterwards, share a drive on the Windows PC connected to the router and mount it on the router with a command in the shell that should look like this: ‘mount -t cifs //192.168.70.63/testshare /martin -o unc=\192.168.70.63testshare,ip=192.168.70.63,user=martin,pass=xxxyyyzzz,dom=workgroup‘.
192.168.70.63 is the IP address of the router and ‘testshare’ is the directory I’ve opened for network sharing. Make sure the user name and password given in the command are correct. If you don’t know the domain of your PC it’s probably the default domain name ‘workgroup’. If the command succeeds a new command prompt without a further message appears.
Change the directory to the mount point and verify the share is mounted correctly by putting a couple of files into the Windows directory with the file explorer and by doing an ‘ls -l‘ on the router. They should then be visible on the router.
Note: ‘mount’ doesn’t give very detailed error messages in case something goes wrong. In case you encounter problems, make sure first of all you have set the Windows firewall to allow network and printer sharing on the local LAN.
Note 2: The share has to be remounted after the router has been rebooted.
Installing Kismet
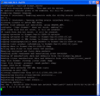
Hold your breath we are almost there now. The final step is to install Kismet. This is done by typing ‘ipkg install kismet-server‘ and ‘ipkg install kismet-client‘. Once done, change into the directory in which the share of the PC is mounted and type ‘kismet_server‘ (note: underline!). Kismet will then start and output a number of messages as shown on the left. Open a second ssh window and start the client by typing ‘kismet_client‘. The client automatically connects to the server and displays an overview of the number of networks found, packets received, etc. On the PC take a look at the shared directory. You should see a number of new files created by Kismet. The most important one is the .dump file which contains all packets received by Kismet. Once enough packets are collected, press ‘CRTL-C’ in the kismet server ssh window to stop the server. Afterwards, rename the ‘.dump’ file into ‘.pcap’. If you’ve already installed Wireshark on the PC you can now double click on the file to open Wireshark to display the captured frames. If you haven’t installed Wireshark so far, download it from here.
Here we go, that’s it! Not quite a solution that works out of the box straight away but with some prior Wifi configuration experience and a bit of Linux experience not to difficult to do. Have fun!