In case you have an Nokia N95 or similar SIP capable 3G / Wifi / VoIP phone and wondered why the little icon during a VoIP call shows an ‘open lock’, the answer is simple: The encoded voice data is not end-to-end encrypted. That means that anyone on the network between you and the other party who can intercept the data packets can listen to your conversation.
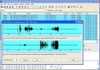
Sounds difficult to do in practice? Well, not really. I recently discovered that Wireshark, a free network monitoring tool, can decode G.711 PCM encoded speech data of SIP VoIP calls as shown in the picture on the left.
Just to be clear, this is not the fault of Nokia as I haven’t seen any other SIP client in practice yet that encrypts the voice data stream. In a public Wifi hotspot, intercepting the call and listening to the conversation is very simple, as the data packets are not encrypted between the device and the Wifi access point. In home networks, things get more difficult because most people nowadays have encryption between their devices and the Wifi access point enabled. But do you know what happens on the other side of your DSL connection…?
Martin,
Yes, sadly, almost all SIP clients out there are using unencrypted RTP. Secure RTP (SRTP) is out there, but for a variety of reasons is not widely deployed at all. Wireshark is just one of many tools that are out there that let you listen in to RTP streams if you can get between the sender and receiver. Over at the VoIP Security Alliance (VOIPSA), we’ve compiled a list of many tools at:
http://www.voipsa.org/Resources/tools.php
As you point out, usage of SIP clients at public WiFi hotspots does leave your audio stream wide open to interception if anyone is running a packet sniffer in that hotspot.
Hopefully over time we’ll see more people realize this issue and ask for/demand SRTP for secure voice. But right now, it’s all wide open with few exceptions.
Dan