When always going from one smartphone model to the next it is often difficult to see how things have advanced as the differences are often only subtle. But when comparing devices that are three or four generations apart one can see a real difference. Taking web browsing speed for example between, a two year old Nokia N8 with OperaMIni and a current high end model such as a Samsung Galaxy S-III. When clicking on a link on the N8 it takes a second or two for the new page to show up, even on mobile optimized pages. A good browsing experience, no doubt, but totally shadowed by the web browser's speed on the S-III where the page is displayed almost instantly, even when the radio connection has been in a dormant state to conserve power. This speed-up is really impressive. Now give me world wide offline maps & navigation and a superb camera, two things I like on my N8 and I am ready to move one.
Month: September 2012
There Is No Such Thing As Free Wi-Fi In Hotels
In the past most hotels charged extra for Wi-Fi Internet connectivity and while today some still do there is a growing trend to offer it for free. I wonder, however, what the motive is behind this trend.
More often than not, this "free" Wi-Fi Internet access is shoddy at best and doesn't work at all during busy times, i.e. in the evenings when people come back to their rooms. There are several reasons for this ranging from low signals to under dimensioned backhaul. During daytime, downlink speeds might exceed 10 MBit/s but when testing the uplink I seldom get more than 1 MBit/s. These numbers tell two stories: For one, it shows that no sort of traffic shaping is applied that could help handle the load when many users are online. And second, the uplink is the real problem as it saturates very quickly when the number of users increases taking downlink performance with it. A deadly combination for any network. But even with traffic shaping a 1 MBit/s uplink or even less is just not enough these days, when every hotel guest seems to bring at least 3 Wi-Fi capable devices ranging from notebooks over smartphones to tablets.
So "offering the Wi-Fi for free" is perhaps just the realization that you can't ask for money for something that regularly breaks down. Too much trouble with the guests. So I regularly go back to my 3G connectivity solution which is not free, but it works, at least in those countries with affordable local or roaming rates.
My Own OpenVPN Gateway at Home for 38 Euros
When traveling, I often use VPN tunnels to secure my data transfers e.g. in open Wi-Fi hotspots or to prevent cellular network based transparent "optimization" algorithms from compressing webpages and pictures. There are a number of companies out there that offer gateways around the world and good OpenVPN support. However, one thing I can't do with them is to securely access my resources at home (e.g. my NAS). Also some countries I travel to block access to their public gateways. For both reasons, I long wanted to set up my own OpenVPN Gateway at home. Finally, I had some time to my surprise the necessary hardware, a Linksys WRT-54GL can be had for 38 Euros. An OpenVPN gateway at home for 38 Euros, I call that a good price.
It was a bit tricky to get the gateway up and running though, I spent the better part of three evenings to get things working. Let's count it as part of the adventure. 99% of how to get the gateway up and running can be found in this post on How-To-Geek. One of the best tutorials on how to set-up something complex I have ever seen. Highly recommended. In short it works as follows:
- Get a Linksys WRT54GL router or any other router on which the open source DD-WRT Linux can be installed.
- Install the OpenWRT client, preferably on a Windows machine as the tutorial linked above shows how to do it on this OS, and use the tools that come with the software to generate a number of keys and certificates needed for the OpenVPN server and client. This is the tricky part but the tutorial describes it in detail.
- Copy/paste the required certificates to the OpenVPN router. One point that's not contained in the tutorial is that some of the key and certificate files created contain some explanatory text that must not be copied/pasted into the OpenVPN configuration. If done, the configuration won't be saved in the router.
- Make the OpenVPN server thread start automatically. As I use my DSL router as a gateway to the Internet, a number of configuration steps are required that are not described in the tutorial. As the VPN tunnel uses its own IP address subnet, it is necessary to create a static route to this subnet in the DSL router's IP configuration. Also, the NAT firewall has to be configured to forward UDP port 1194 to the VPN gateway router (I decided not to use TCP as described in the tutorial). And finally, for some strange reason, the OpenVPN server thread does not start automatically in my setup, probably because I don't use the WRR54GL box as an IP gateway with NATing. This can be fixed by adding the following command to the startup commands in the router GUI:
openvpn –config /tmp/openvpn/openvpn.conf –route-up /tmp/openvpn/route-up.sh –down /tmp/openvpn/route-down.sh –daemon
- Disabling Wi-Fi: As I only want to use the router as a gateway there is no need for the Wi-Fi access point running. Unfortunately, there is no GUI option to disable Wi-Fi and I couldn't come up with a clean solution for it. There is a command to disable the Wi-Fi. However, if executed as a startup command the router ends up in a reboot loop. The kludge that works for me is to run the disable Wi-Fi command as a cron job periodically. Here's the line for the cron job:
*/5 * * * * root wl radio off
- Partial or Full VPN: The VPN tunnel can be used for tunneling only the traffic for the home network or as a full IP tunnel depending on how the client is configured. In full tunnel mode (the tunnel is used as a gateway to the Internet) all traffic is sent over the tunnel into my home network and from there to the Internet. When using the tunnel to encrypt all traffic one additional manual setting required in the client is the DNS server as it's not configured when the tunnel is established. An easy solution is to use Google's DNS server IP address (8.8.8.8).
- Windows Clients: I got the setup working just fine with Ubuntu 12.04 as a client machine. I also tried Windows 7 and Windows XP but couldn't get the tunnel working. It establishes just fine but no data is flowing through it, not even to server side IP address. Very strange as the tutorial was written for Windows 7. But it's not my primary platform anyway so I grinded my teeth and ignored it for the time being.
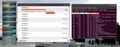 Performance wise, the 200 MHz ARM processor in the router has its limits. The processor maxes out at a throughput of around 4.5 MBit/s as shown in the picture above. At this speed, the OpenVPN server thread takes 98% of the CPU time. My current VDSL uplink speed is 5 MBit/s so I am close to the limit. More up to date and more expensive routers that can run DD-WRT will probably do even better as they have much more capable ARM processors and clock rates of 600 MHz and beyond. As not the downlink speed of the DSL or cable connection is the limit but uplink line rate, which is usually much slower, the old low cost WRT54GL router will do just fine for most people.
Performance wise, the 200 MHz ARM processor in the router has its limits. The processor maxes out at a throughput of around 4.5 MBit/s as shown in the picture above. At this speed, the OpenVPN server thread takes 98% of the CPU time. My current VDSL uplink speed is 5 MBit/s so I am close to the limit. More up to date and more expensive routers that can run DD-WRT will probably do even better as they have much more capable ARM processors and clock rates of 600 MHz and beyond. As not the downlink speed of the DSL or cable connection is the limit but uplink line rate, which is usually much slower, the old low cost WRT54GL router will do just fine for most people.
There we go, infinite possibilities opening up with my new VPN gateway and I learned a lot in the process of making it work.
Finally An Update I Liked
Most of us don't like change, especially when it comes to computers. Most people like what they have and dread security or feature updates because they could break something that already works. But they are a necessary "evil" because security updates keep us, well, more secure and feature updates in the majority of cases improve computing. I can well remember the days of DOS and there's no way I ever want to go back there so at least some of those at first unloved updates do something good in the long run.
But still, most updates are a pain and I can't remember when I last updated something because I really wanted to. But now I have at least one counter example. Recently, I noticed that the latest version of TightVNC, a remote desktop viewer I've been using for a decade at least was finally integrated to run as a service in Windows 7. What sounds benign at first turns out to be a major productivity increase. Ever since Windows 7 appeared on the computers I remotely administer, I couldn't do some things without human intervention on site as all security confirmation dialog boxes were off limits to user level programs. Very frustrating at times. So now TightVNC runs as a service and I can remotely acknowledge security notifications, I can even reboot and log on from the login screen. I'm ecstatic, finally an update I like! Time for Windows 8 to mess things up again.
Why BYOD Is Nothing For Me
There is this new supposed trend call "Bring Your Own Device", or BYOD for short, meaning you use your own personal devices at work and for work. It's probably the nightmare of every company network administrator because how do you ensure data security and confidentiality on devices you don't really have under your control. Their nightmares are perhaps lessened a bit as companies introduce methods to encrypt data and control data remotely, i.e. company network administrators can remotely wipe devices or at least the company parts of it should it become necessary and are probably also aware of the device's location, etc. And this is the point where I stop liking BOYD.
I fully embrace the idea that a device I buy is mine, it's under my control and I can do with it what I want. This is why I don't have an iPhone, it's not mine when I buy it, it's still controlled by Apple. No thanks. And even the mere thought of a company I work for having access to a device I own counters this very notion of being mine and being in control.
Perhaps BYOD can evolve a bit so I might have a second look!? How about a virtual machine in a mobile device running an encrypted OS with company applications? The host device is mine, the host OS and applications are mine but the content of the virtual machine is managed by the company. If I don't like what the company is doing, I get rid of the VM container. If the company needs to delete the data, they delete the virtual container. Done. A clear separation of control. I am not sure however if it would work from a security perspective as the host OS or an application running in the host OS could still access the memory of the virtual machine and thus maliciously extract data. But if that could be prevented, well, perhaps it might be worth a second look.
Virus Scare and Linux Happiness
In many many years a close friend's Windows 7 computer remained free of malware and we did a lot to keep it that way. Updating Flash, Java, Windows, Firefox, Thunderbird, etc. as soon as fixes become available and using an anti virus program should have kept us save. But it didn't and it cost me a full night's sleep to fix it.
Things started to look strange when Google searches sometimes did not end up on the selected page in the search results but the browser was instead redirected to a completely different page. When looking at it I saw that Google showed the references to the page correctly but when clicking on the link there were suddenly a number of redirections to pretty strange URLs indicated at the bottom of the window before a final destination was selected . It wasn't a rouge browser plugin as the same process repeated itself when using Internet Explorer as well. This looked like click fraud to me because the final pages were those of big and well known companies. Then I noticed that Microsoft's Security Essential virus scanner was not running anymore and restarting it manually ended up in an error message. Now that made it pretty clear that something is really wrong.
So I shut down Windows and booted to a special Ubuntu virus scan CD. I always carry it with me hoping tat I would never have to use it. Now I'm glad I carried it along. During several hours of scanning over night it revealed a number of infected files with two viruses. After removing them and rebooting, things in the browser were back to normal. Microsoft Security Essentials still didn't work but reinstalling the package fixed this. Then I discovered that the malicious program had also deactivated the Microsoft Notification service so it wouldn't complain that the anti virus was not running.
How could this have happened? The bad thing is that without the virus scanner having detected it there is no way of telling. A drive by virus on a web page using an unknown weakness, something in an attached document of an email? Lets hope the updated virus definitions will catch it next time or a patch against it has been installed in the meantime because without knowing where it came from there is little that can be done to prevent it from happening again.
Another nail in the Windows coffin on that machine and one more reason to switch to Linux for my friend. After all, Windows 8 will be so different she needs to relearn the desktop anyway. It's time to change.
Thalys Internet Access Continues To Be A Joke
During the past couple of Thalys train trips from Cologne to Paris I just ignored the “we have Wi-Fi Internet access on board” announcements since it just didn't work anymore even though at the beginning they had a brilliant start. Whenever I tried there was just no connectivity at all except for the landing screen. But they keep insisting during their automated welcome messages that Internet access is available. O.k., I believe in the good and in things getting better so I tried again on my recent trip. Again, it didn't work. What a letdown!
Dear Thalys, just switch your Wi-Fi off and stop this ridiculous announcement as it's obviously not your intention to improve the situation. This way, your customers will at least not be disappointed by something they are promised. Just admit you've failed and move on.
P.S.: Note that this is not a technical issue, it worked great at the beginning. Also other train companies such as Deutsche Bahn show that working Internet access on high speed trains is possible.
Three Friends in Femtoland
When I was recently on vacation I visited friends and incidentally they all lived just outside of smaller towns on the countryside. They all had a DSL line at home but mobile network coverage was weak at best. Apart from being a nuisance for me they said themselves that they were not happy with the mobile network coverage in their house. And it was not like they were living in totally remote areas. Perfect places for femto cells!
So while femtos haven't really made a big inroad in most countries over the years so far, I still see the potential and the need, especially since people more and more use their mobile phones instead of fixed line devices for voice calls. Sure, Wi-Fi and SIP clients could also do the trick on their devices when they are at home but it's not seamless and doesn't work for their guests. Fortunately, Vodafone seems to expand their femto solution to more countries beyond the UK now so let's see, perhaps that might be a solution for such locations and perhaps a reason for the competition to wake up.
Forget 3G and 4G, Let’s Call It What It Is
In recent comment to a blog post, Sergey observed that the usage of the terms 3G and 4G is completely different in the US and Europe. While in the US, the term 4G is used instead of LTE, it's exactly the opposite in Europe, where the term 4G is not very prevalent and LTE is used in the mainstream press. Both parts of the world have reasons from a marketing point of view to do one thing or the other. And by the way, some even call UMTS networks 4G in the US. And to dazzle you even more, a well configured dual carrier UMTS network can easily compare with a 10 MHz LTE network, the prevalent bandwidth in the US, or even surpass. And to drive the point home, a 20 MHz LTE network in Europe easily beats a 10 MHz network in the US. There we go, the terms 3G, 4G are completely meaningless but unfortunately suggest that one thing is better than the other when even 4G can't be compared to another 4G network.
So perhaps we have to go back to the roots? Perhaps everything based on UMTS should be called UMTS and everything based on LTE should be called LTE, at least by engineers who know what they are talking about!? And if you really want to compare performance, the terms won't help much just like the terms 3G and 4G. But at least they don't have this bias in them intrinsically that suggests one is better than the other. Well, and if one really discusses performance, then one has to to pull out lots of parameters such as bandwidth used, modulation and coding schemes available, cell site density, backhaul capacity, etc., etc., irrespective of the technology used.
100 Petabytes of Facebook
Recently, Techcrunch and Gigaom reported a couple of very interesting technical details on the amount of data and number crunching over at Facebook. Here are some:
- Current amount of data stored: 100 petabytes. That is 100.000 terabytes! Imagine the physical amount of space required to store such an amount of data…
- 500 terabytes (i.e. 0.5 petabytes) of data added each day, including 300 million new pictures.
- 105 terabytes of data analyzed every 30 minutes.
Anyone's got a link to original material on this, I'd like to hear/see it from them first hand!?
If 0.5 petabytes are added per day that's 182.5 petabytes per year if user behavior stays the same even without adding new users. Makes one wonder how long they can keep up with the amount of data they have to store as cost for it will rise as well. I wonder if the storage and power costs per TB of data is decreasing as fast their data store is increasing. Kind of a life and death question if you don't want to throw away data at some point unless you can increase your revenue at the same time with storing more and more data.