![]() Once upon a time, a hotel chain thought it would be a good idea to sabotage Wifi hotspots of their customers. The FCC didn’t like it at all and stepped in and the practice fortunately ceased. But others may still think this is a good idea and could actually get away with it unless access points and mobile devices would start implementing Protected Management Frames (PMF). This was all back in 2015 and 2016 but since then I haven’t seen access points that actually implement the protection in the wild. But now my Fritzbox 7590 Wifi access point at home supports the feature so I had a look how clients behave with and without PMF activated.
Once upon a time, a hotel chain thought it would be a good idea to sabotage Wifi hotspots of their customers. The FCC didn’t like it at all and stepped in and the practice fortunately ceased. But others may still think this is a good idea and could actually get away with it unless access points and mobile devices would start implementing Protected Management Frames (PMF). This was all back in 2015 and 2016 but since then I haven’t seen access points that actually implement the protection in the wild. But now my Fritzbox 7590 Wifi access point at home supports the feature so I had a look how clients behave with and without PMF activated.
So here is how the PMF feature works in practice: So far, Wifi management frames are not protected which means that a malicious actor can send deassociation frames to a device by forging the MAC-address. This in effect kicks out the device from the network. To protect against this and other attacks, the idea that the IEEE 802.11 committee has come up with was to protect, i.e. encrypt, the management frames as well with the per-user session key. If the access point supports this it, announces this capability in its beacon frame in the RSN Capabilities field. The first image on the left at the beginning of the post shows this part of the beacon frame of my access point with the ‘PMF-support’ bit being set (click to enlarge).
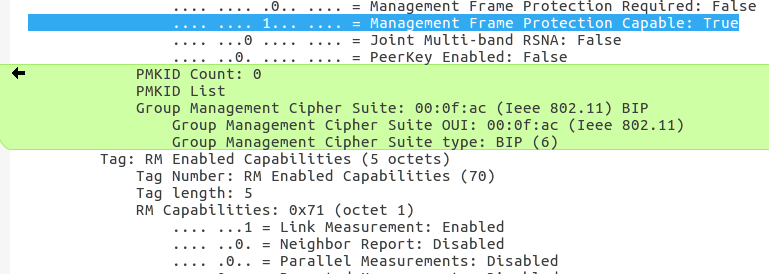 If a mobile device supports PMF, it indicates this in the Association Request message when it first connects to the Wifi network and includes additional ciphering capability information for the management frames. The second image on the left shows how this is looks like in practice. Like in the beacon frame, there is also a PMF-support bit that is set independently of whether PMF support is announced by the access point or not. If the access point supports PMF, the device additionally includes further information in the PMKID parameter which is otherwise absent. I’ve marked this part green in the image on the left.
If a mobile device supports PMF, it indicates this in the Association Request message when it first connects to the Wifi network and includes additional ciphering capability information for the management frames. The second image on the left shows how this is looks like in practice. Like in the beacon frame, there is also a PMF-support bit that is set independently of whether PMF support is announced by the access point or not. If the access point supports PMF, the device additionally includes further information in the PMKID parameter which is otherwise absent. I’ve marked this part green in the image on the left.
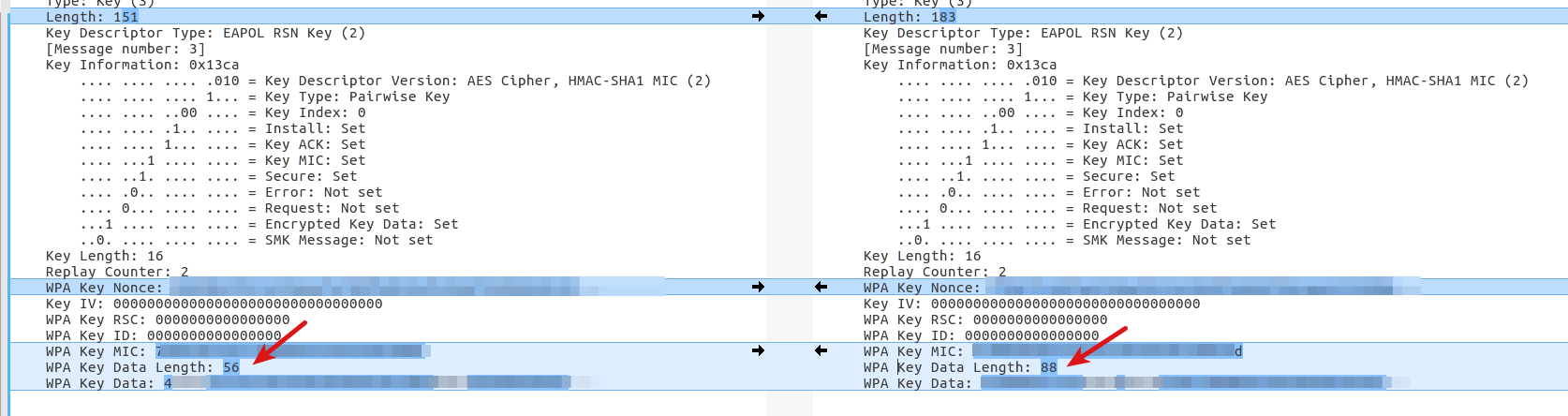
The access point then uses this information during the WPA EAPOL authentication and ciphering procedure to return additional WPA key data for protecting the management frames. The third image on the left shows a comparison of the 3rd frame of an EAPOL exchange with and without PMF ciphering information included. On the left, the WPA key data length is 56 bytes while on the right with PMF activated, 88 bytes are sent from the access point to the mobile device.
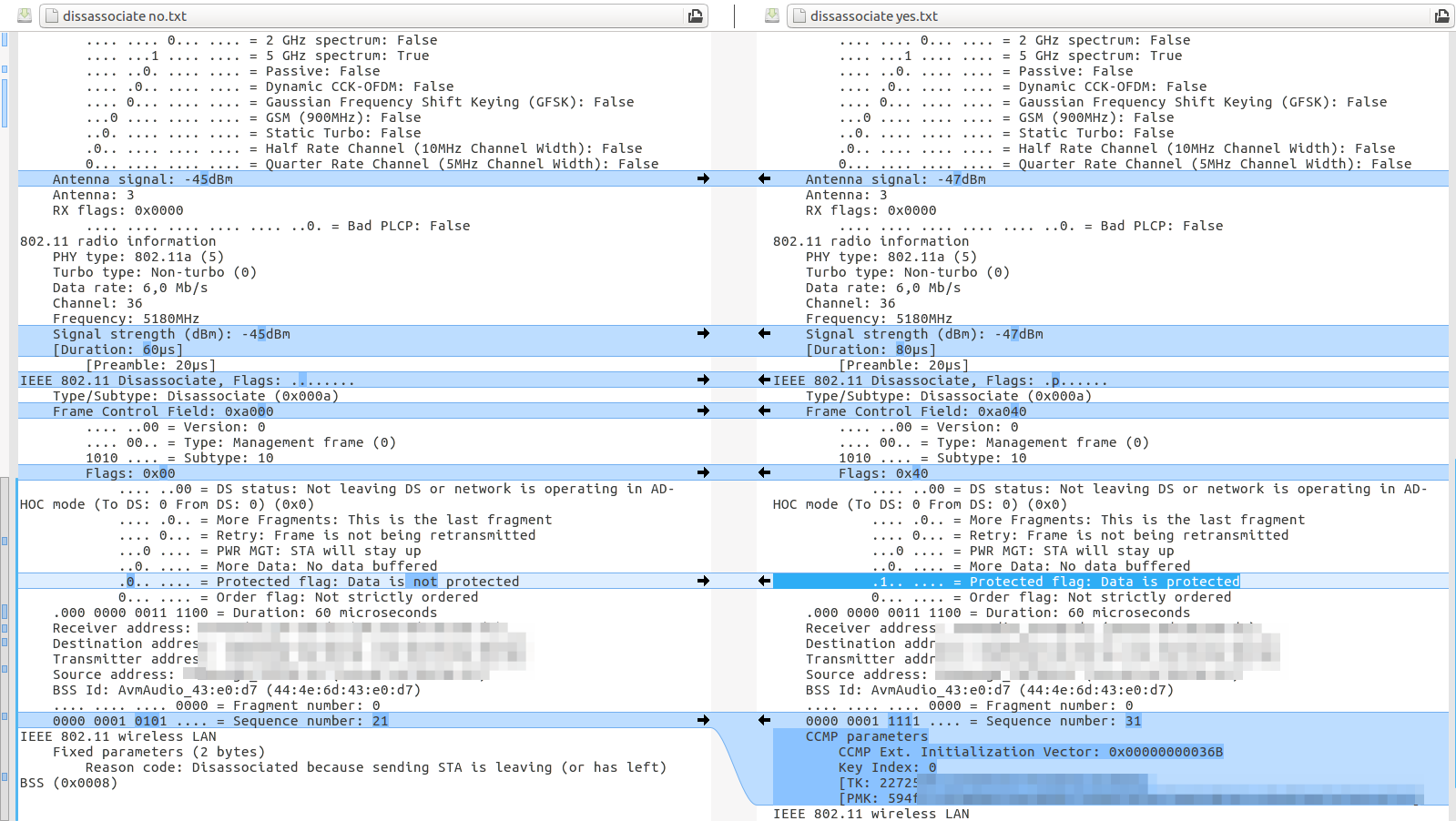
And finally, here is a comparison of a disassociation management message with and without PMF protection:
 If implemented correctly, and lets assume everybody has gone the full mile here, unencrypted disassociation management frames are simply ignored for connections that have PMF activated. For backwards compatability an access point supports PMF and non-PMF devices simultaneously, unless PMF is configured as mandatory (which is not possible on my Fritzbox 7590).
If implemented correctly, and lets assume everybody has gone the full mile here, unencrypted disassociation management frames are simply ignored for connections that have PMF activated. For backwards compatability an access point supports PMF and non-PMF devices simultaneously, unless PMF is configured as mandatory (which is not possible on my Fritzbox 7590).
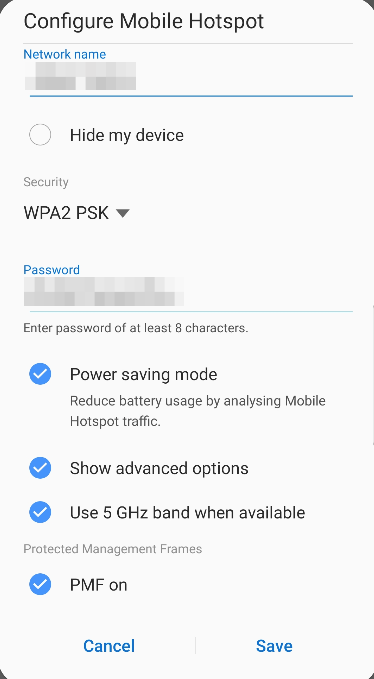
And even better, I have noticed that not only does my Wifi router at home support PMF these days but also my smartphone I use for Wifi tethering. It is disabled by default but can be activated in the advanced hotspot settings! For further technical details on the topic have a look at this excellent post.