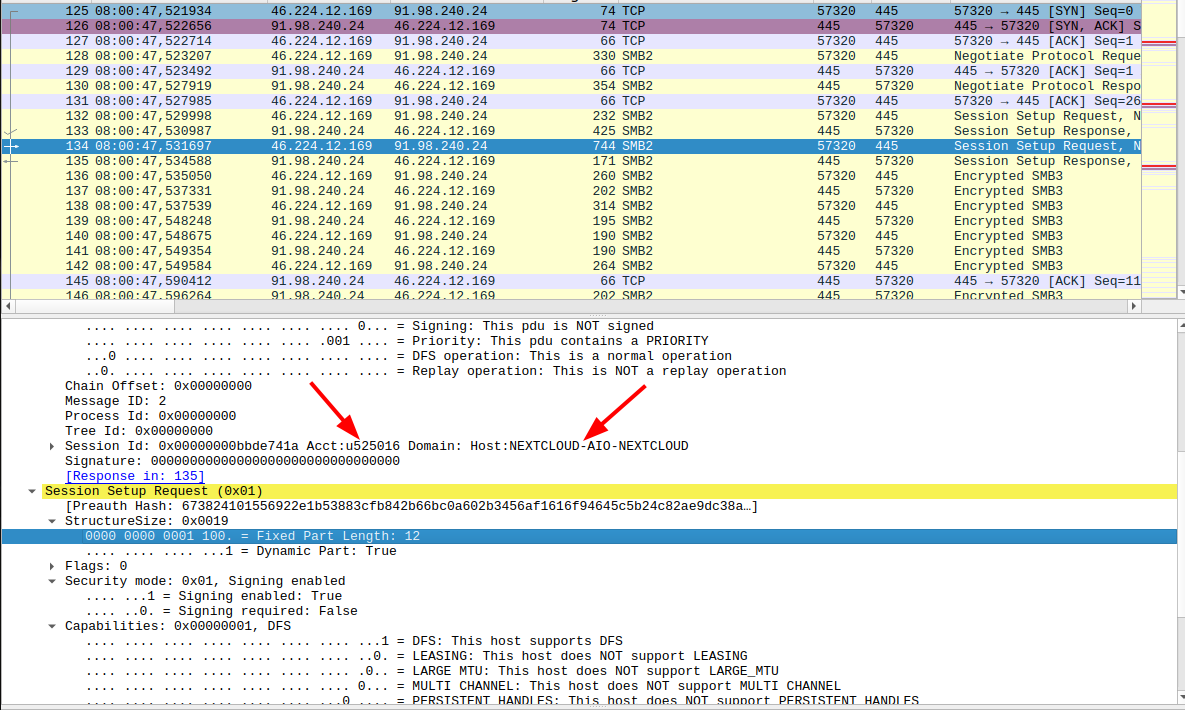
And a quick follow up to a previous post on using Nextcloud ‘external’ storage on another host over an SMB network mount: SMB / CIFS seems to have been a bit ‘insecure’ in the past, so using it over the Internet was not recommended. However, recent versions of SMB, particularly version 3, seems to have the necessary authentication and encryption features to make this feasible. I was curious of course so I decided to run a tcpdump on my Nextcloud machine to see how the traffic to my SMB server looks like.
As you can see in the screenshot above, I did find the username (u25016) and client software name (NEXTCLOUD-AIO-NEXTCLOUD) in the clear. Everything else, however, seems to be encrypted and I didn’t encounter any file or directory names. Also, I didn’t come by any file content in the clear. I’m no crypt expert but at least I didn’t stumble over something obvious with little effort. So in combination with client side encryption (see previous post), this seems to be OK for use. And if it was my own SMB server and not a Hetzner storage box, I’d probably run all traffic through a Wiregard VPN and make sure the SMB server would only be accessible through that tunnel and not from the Internet.