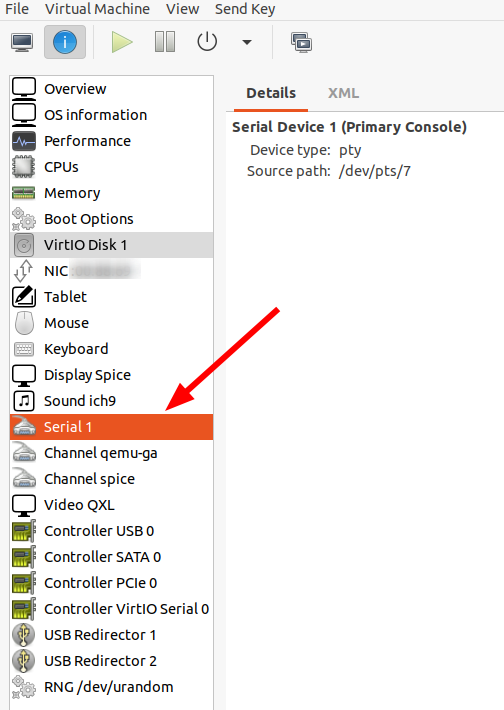
When you are working with virtual machines in the cloud, I’m sure you’ve come across a situation in which you thought you had a great idea to reconfigure the network stack and ended up with the VM not being reachable anymore. As a last resort, one can always turn to the virtual machine manager and open a virtual display and log-in. When it comes to KVMs Virtual Machine Manager GUI, however, the display functionality is quite rudimentary, one can’t even copy/paste text to and from it. Especially when making larger changes on a config file, that’s quite a showstopper. But there’s another way: A virtual serial console!
Continue reading Bare Metal Cloud – Part 4 – Getting a Serial Console When the Network is Broken