In the past, Wifi networks were criticized a lot for being insecure. In the meantime, however, the IEEE standards body and the industry have reacted and designed WPA and WPA2 (Wireless Protected Access) which is implemented in most products today. WPA and WPA2 deal with both authentication and ciphering and a lot of information is available on the net about the ciphering part. Information on the authentication part, however, is scarce. Time to change this:
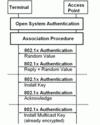
As shown in figure on the left, a client joins a network by performing a ‘pseudo’ authentication and associating to the network afterwards. In a WPA network an additional authentication and key exchange follows this procedure. The first authentication has thus become completely obsolete but has been kept in place nevertheless. The access point announces that WPA is to be used instead of the older WEP (Wired Equivalent Privacy) by including an additional WPA description parameter in beacon frames which are required to inform nearby stations of the presence of the access point. This parameter informs clients that an additional step for authentication and ciphering key negotiation is required after the association procedure. The parameter also contains additional information concerning the algorithms to be used for authentication and ciphering. First WPA implementations use TKIP (temporal key integrity protocol) for ciphering, which is described in more details below. Current devices also optionally support AES (Advanced Encryption Standard), which has become mandatory for WEP2 as also discussed below.
The figure on the left shows the four step process required by WPA in pre-shared key (PSK) mode to authenticate the client to the access point and vice versa. In addition, client and access point agree on ciphering keys during this process, which are used for encrypting user data frames once authentication is complete. In the first message, the access point sends a random number to the client. The client then uses the random number and the pre-shared key, i.e. the password the user types in once, to generate a response. The pre-shared key has a length of 8 to 64 characters. The response is sent back to the access point together with another random value. The access point then compares the response to the value it has calculated with its own secret key. If the secret keys of client and access point are identical the two values match and the client is authenticated. The access point then generates a session key which it then encrypts with the pre-shared key and sends it back to the client. The client uses its pre-shared key to decrypt the session key and acknowledges proper reception in the fourth message. This implicitly activates ciphering in both directions. In a final step the access point then informs the client of the session key used for broadcast frames. This message is already encrypted. While the session keys for individual user data frames are unique for each client, the key for deciphering broadcast frames is the same for all clients because such frames have to be decrypted by all.
By using session keys instead of the pre-shared key for ciphering it is possible to change the session key frequently to prevent brute force key generation attacks. A typical value to negotiate a new session key between the access point and a client is one hour.
Additional information on Wifi and other wireless technologies can be found in my book as advertised on the left side of this blog. And finally, if you like to trace these messages yourself, take a look at this blog entry.