When I’m out and about I’m usually ‘bringing my own Internet’, i.e. I use my smartphone to tether my notebook and other devices. But every now and then I can’t avoid to use a hotel or other public Wi-Fi. And boy was I recently surprised when I used a hotel Wi-Fi that supported Opportunistic Wireless Encryption (OWE). I blogged about this in 2016 (!) but this is the first time I’ve actually seen it in the wild. Truth be told, I have no idea if OWE is something recent in practice or new, as I rarely use public Wi-Fi. But anyway here’s the story how I found it and how it works.
When I was recently at a hotel, I wanted to use their public Wi-Fi but found that little ‘lock’ sign next to their network name in my network list on Ubuntu 22.04. I clicked on the network anyway and started to look around in the room for a note with the password. I couldn’t find one, though, and when I looked on my notebook screen again, I noticed that I was connected to the Internet. Hm, I wondered, how could that be, there was a lock icon, so I should have been asked for a password!? A quick iwconfig revealed the following:
wlp0s20f3 IEEE 802.11 ESSID:"_owetm_XXXXXXXXX566458677"
Mode:Managed Frequency:2.462 GHz Access Point: D0:4D:C6:xx:xx:xx
Bit Rate=26 Mb/s Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
Link Quality=48/70 Signal level=-62 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:3 Missed beacon:0The SSID of the network looked a bit strange, as there were text and digits before and after the network name (XXXXXXX). A quick search on the net for ‘owe wifi’ then gave me the right clue what was going on: Opportunistic Wireless Encryption!
The OWE encryption scheme is defined in RFC 8110 and does not require a password to be typed in. In essence, it is pretty similar to the mechanism used to establish an encrypted https connection between a web browser and server. The major difference is that the Wi-Fi access point does not have a certificate and hence its authenticity can’t be established. That means that a man-in-the-middle attack with a rouge access point is still possible, but passive snooping is not. Not perfect but better than nothing.
Under Linux one can check the syslog or query the wpa status on the shell to get further details and confirmation that OWE is actually used. Nice side effect: With OWE, protected management frames are not only enabled (PMF=1) but actually required (PMF=2)!
$ sudo wpa_cli status Selected interface 'wlp0s20f3' bssid=d0:4d:c6:xx:xx:xx freq=5260 ssid=xxxxxxxxxxxxx id=0 mode=station wifi_generation=5 pairwise_cipher=CCMP group_cipher=CCMP ---> key_mgmt=OWE ---> pmf=2 mgmt_group_cipher=BIP wpa_state=COMPLETED ip_address=172.16.0.80 p2p_device_address=e0:c2:64:xx:xx:xx address=e0:c2:64:xx:xx:xx uuid=xxxxxxxxx ieee80211ac=1
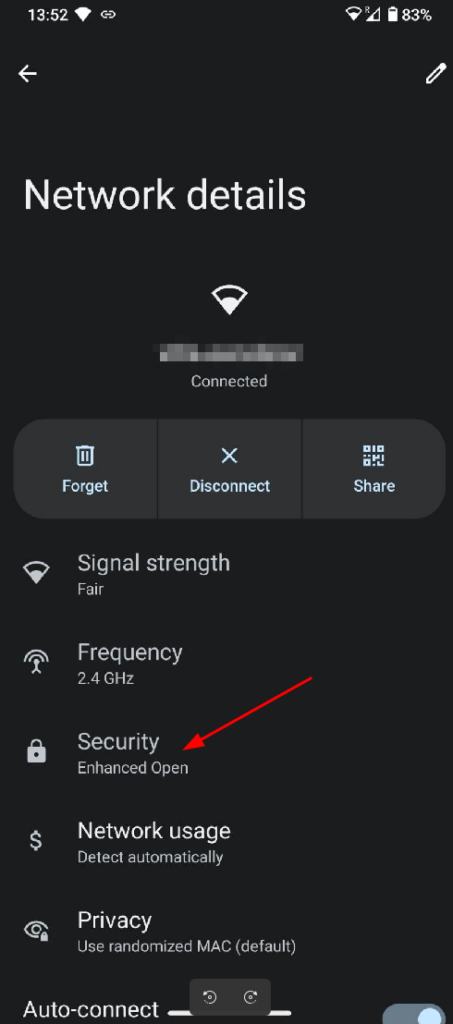
I then also tried this on my Pixel 6 running Lineage OS 20 and also found that it can use OWE with the open Wi-Fi. The screenshot at the beginning of the post shows that this is called “Enhanced Open” security in Android.
So far, so good, so this is how it looks ‘above the line’. In the next post, I’ll have a look at how an access point advertises OWE and how client devices use it.