In the previous post, I’ve taken a first look at how the Opportunistic Wi-Fi Encryption looks like for the user and how one can find out high level details on the shell. In short: OWE enables per device encryption in open Wi-Fi networks without the need to type in a password. In this follow up post, I’ll have a closer look at how OWE is advertised by the Access Point and then picked up by devices.
As not all Wi-Fi devices are OWE capable, there has to be a way to transparently advertise the feature by the Access Point. This is done by broadcasting ‘normal’ beacon frames which include the name (SSID) for the open Wi-Fi network that does not require authentication and offer no encryption. Such beacon frames are understood by all devices. Let’s say the name of the network is ‘Hello-World’ for my examples below. To advertise OWE to supporting devices, the open network beacon frame contains an OWE Transition Mode Tag towards the end of the beacon frame (3GPP enthusiasts would call them ‘Information Elements’). This tag includes, among other things, the network name of this network in which OWE encryption can be activated. The name can be a derivate of ‘Hello-World’ or it can be something completely different. In my example, I’ll use ‘xyz-OWE-Hello-World-123’. So here’s how the parts relevant to OWE look like in beacon frame:
[...]
Tagged parameters (263 bytes)
Tag: SSID parameter set: Hello-World
Tag Number: SSID parameter set (0)
Tag length: 11
SSID: Hello-World
[...]
Tag: Vendor Specific: Wi-Fi Alliance: OWE Transition Mode
Tag Number: Vendor Specific (221)
Tag length: 41
OUI: 50:6f:9a (Wi-Fi Alliance)
Vendor Specific OUI Type: 28
BSSID: d0:4d:c6:xx:xx:xx
SSID length: 30
SSID: xyz-OWE-Hello-World-123In effect, the ‘OWE Transition Mode’ Tag is a pointer to beacon frames with a different name = SSID inside. Devices that do not support OWE simply ignore this tag and are none the wiser. Devices that do support OWE will see the tag and thus know that xyz-OWE-Hello-World-123 is the same network but has OWE encryption. The relevant parts of those beacon frames then look as follows:
[...]
Tagged parameters (291 bytes)
Tag: SSID parameter set: xyz-OWE-Hello-World-123
Tag Number: SSID parameter set (0)
Tag length: 30
SSID: xyz-OWE-Hello-World-123
[...]
Tag: RSN Information
Tag Number: RSN Information (48)
Tag length: 26
RSN Version: 1
Group Cipher Suite: 00:0f:ac (Ieee 802.11) AES (CCM)
Group Cipher Suite OUI: 00:0f:ac (Ieee 802.11)
Group Cipher Suite type: AES (CCM) (4)
Pairwise Cipher Suite Count: 1
Pairwise Cipher Suite List 00:0f:ac (Ieee 802.11) AES (CCM)
Pairwise Cipher Suite: 00:0f:ac (Ieee 802.11) AES (CCM)
Pairwise Cipher Suite OUI: 00:0f:ac (Ieee 802.11)
Pairwise Cipher Suite type: AES (CCM) (4)
Auth Key Management (AKM) Suite Count: 1
Auth Key Management (AKM) List 00:0f:ac (Ieee 802.11)
Opportunistic Wireless Encryption
Auth Key Management (AKM) Suite: 00:0f:ac
(Ieee 802.11) Opportunistic Wireless Encryption
Auth Key Management (AKM) OUI: 00:0f:ac (Ieee 802.11)
Auth Key Management (AKM) type:
Opportunistic Wireless Encryption (18)
[...]
Tag: Vendor Specific: Wi-Fi Alliance: OWE Transition Mode
Tag Number: Vendor Specific (221)
Tag length: 26
OUI: 50:6f:9a (Wi-Fi Alliance)
Vendor Specific OUI Type: 28
BSSID: d0:4d:c6:5e:e9:13
SSID length: 11
SSID: Hello-WorldInteresting: These beacon frames also contain an OWE Transition Mode tag, which points back to the open beacon frames that can be used by legacy devices, without encryption of course.
And that’s already it on the brodcast level, i.e. the beacons. Devices that are not OWE capable probably show both SSIDs. All devices I had with me when I saw this were OWE capable and all of them only showed the ‘Hello-World’ network while suppressing the “xyz-OWE-Hello-World-123” network name. Linux, however, shows the SSID after being connected on the shell as shown in the previous post. The device then connects to the network with a 4-way OWE authentication handshake as described in more detail here. With Wireshark this looks as follows:
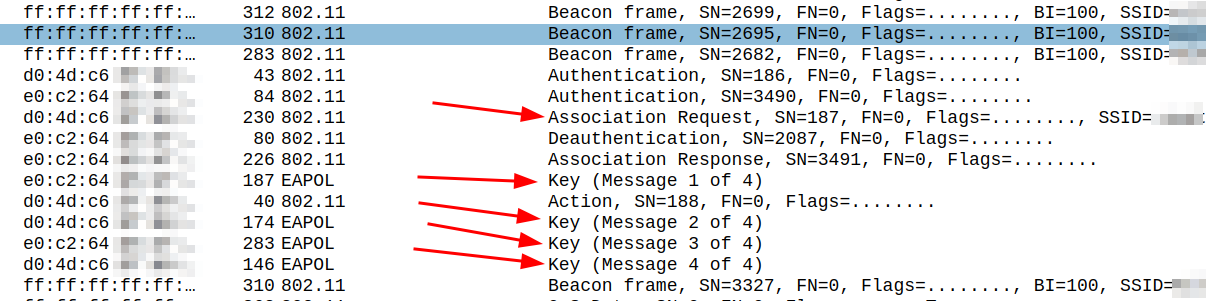
And inside the ‘Association Request’ packet, OWE is requested as follows:
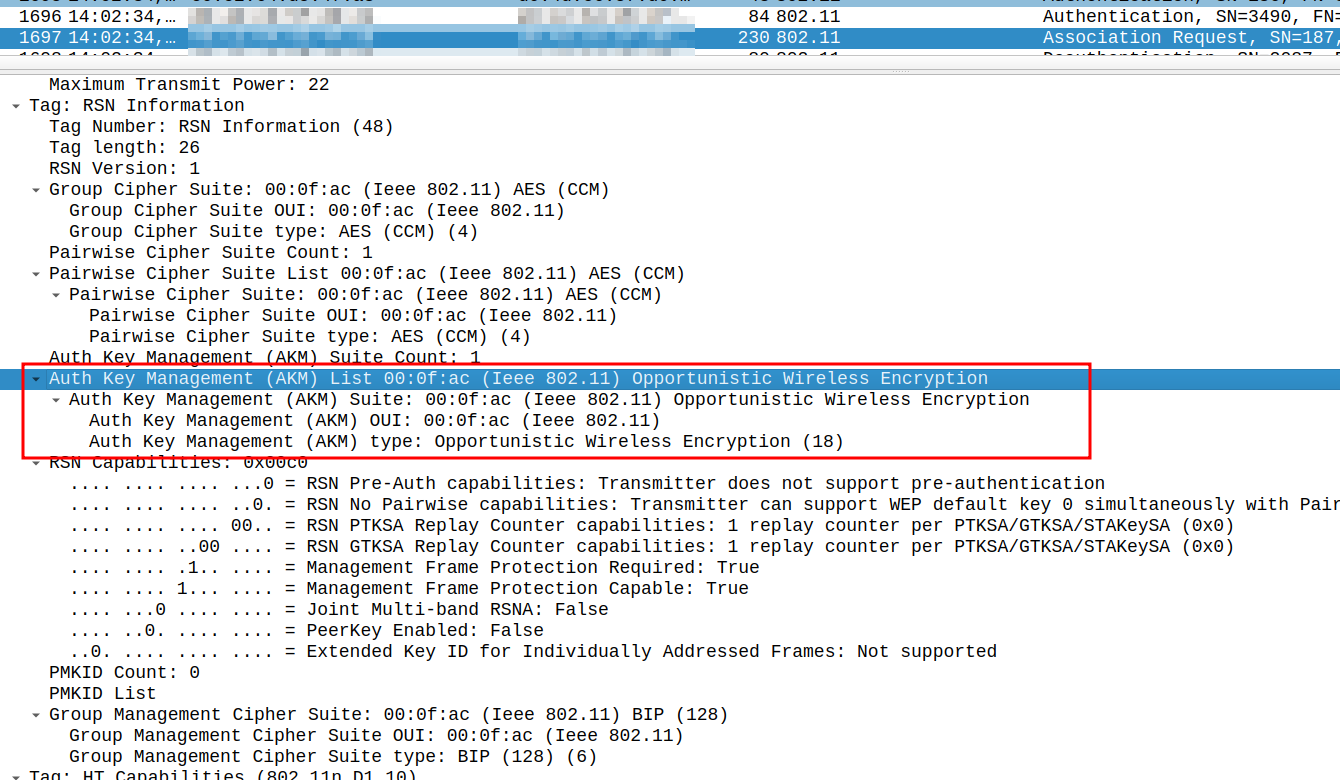
Bonus: When using OWE, protected management frames are mandatory! For details why this is great, have a look here!
Se here we go, that’s it, OWE in action!