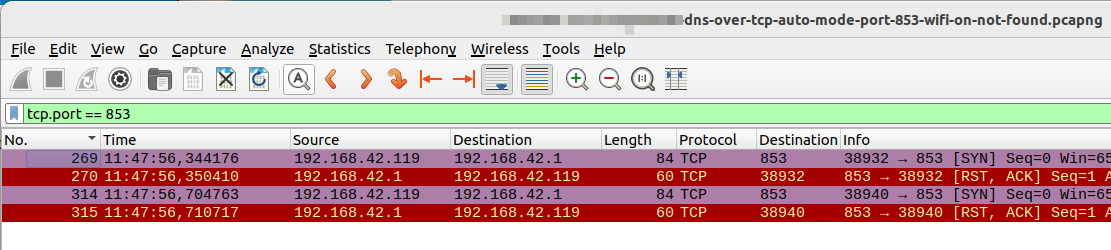
Recently, I had a look if and how Android uses DNS over TLS (Transport Layer Security), i.e. encrypted DNS queries, and if this is actually configured automatically. It turns out that there is a simple yet nifty automatic procedure in place.
By default, Android uses the age-old tried and tested DNS mechanism by sending DNS requests over UDP to the DNS server(s) given in DHCP (Dynamic Host Configuratin Protocol) answers for Wi-Fi or as part of PDU Conntext / Session Establishment procedure in LTE/5G networks. In a second step, Android then takes a look if these DNS servers also support DNS over TLS. It does this by trying to establish a TCP connection to port 853 to these DNS servers. If that works, DNS continues over the encrypted link. The screenshot above shows how this works in practice. As I don’t have DNS over TLS on my DNS server, the TCP SYN request is rejected and DNS requests continue to be transported over UDP.
Note that it is also possible to manually configure the IP address of a DNS over TLS server manually, something I’m sure at least 0.01% of users will do. Sarcasm aside, I’m happy the option exists. I then had a look to see if there is a similar mechanism on iPhones. But it looks like there is not, so this seems to be an Android specific feature. Please let me know if I’m wrong or if this becomes available in the future.
Obviously, an adversary can prevent DNS over TLS from starting by intercepting packets to TCP port 853 and closing the connection. This, however, requires a man-in-the-middle attack, which is much harder to do than just passive sniffing.