In a previous post, I’ve been looking at how authentication is performed in WPA enabled Wifi networks. A growing number of GSM and UMTS devices now also include Wifi as an alternative access technology and if cellular operators decide to run Wifi hotspots, a convenient way must be found to authenticate these hybrid devices there as well. A number of different solutions exist but most of them require the user to input information. To remove this user interaction, an authentication method now known as EAP-SIM was recently specified in RFC 4186. With EAP-SIM, user interaction is no longer required when the device registers to the Wifi network, as all required authentication information is taken from the SIM card. Here is how it works:
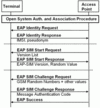
EAP-SIM uses the same authentication framework as described for WPA personal and enterprise authentication. The figure on the left shows the messages exchanged between the mobile station and the authentication server via an EAP-SIM capable access point during authentication. After the Wifi open system authentication and association, the access point starts the EAP procedure by sending an EAP Identity Request to which the mobile device has to respond to with an EAP Identity Response message. The identity returned to the network in this message is composed of a identity type identifier, the IMSI (International Mobile Subscriber Identity), which is taken from the SIM card, and an operator specific postfix. Alternatively, the mobile device can also send a temporary identity (pseudonym) which has been agreed with the network during a pervious authentication procedure. The pseudonym is similar to the TMSI (Temporary Mobile Subscriber Identity) used in GSM networks but has a different format and is used to hide the subscriber’s real identity from eavesdroppers.
In the next step, the network sends an EAP SIM Start request which contains a list of different versions of supported EAP SIM authentication algorithms. The client device selects one of the algorithms it supports and sends an EAP SIM Start response message back to the network. This message also contains a random number which is used for a number of subsequent calculations on the network side in combination with a secret (the Kc) which is shared between the mobile device and the network. This way the network is also able to authenticate itself to the client.
At this point the authentication server in the network uses the subscriber’s IMSI to request authentication triplets from the GSM/UMTS Home Location Register (HLR) / Authentication Center (AuC) (cp. e.g. Chapter 1.6.4 of my book). Two or three GSM random values and GSM ciphering keys returned by the HLR are then used to generate EAP SIM authentication keys, EAP SIM encryption keys and other values required for the EAP-SIM authentication process. These are sent in encrypted form together with the two or three GSM random values in plain text to the client device in an EAP SIM Challenge request to the mobile device.
The mobile device then uses the GSM random values received in the message and forwards them to the SIM card. The SIM card then generates the GSM Signed Response and GSM ciphering keys which used afterwards to decipher the EAP SIM parameters received. If those values are identical to the values used by the network, the mobile device is able to send a correct response message which is then verified on the network side. If verification was successful an EAP Success message is returned and the client is admitted to the network.

The second figure on the left shows the different devices and protocols used during authentication. On the left side the mobile client sends its EAP messages via the EAPOL protocol. For the messaging between the access point and the authentication server, the RADIUS protocol can be used. The authentication sever finally communicates with the HLR/AuC via the SS-7 circuit switched signaling network and the Mobile Application Part (MAP).
Currently, only few Wifi hotspot networks run by cellular operators support EAP-SIM authentication. One that does already, however, seems to be the hotspot network run by Swiss Mobile, as they announce it as part of the network name and also sell EAP-SIM compatible combo GPRS/UMTS/Wifi cards.




