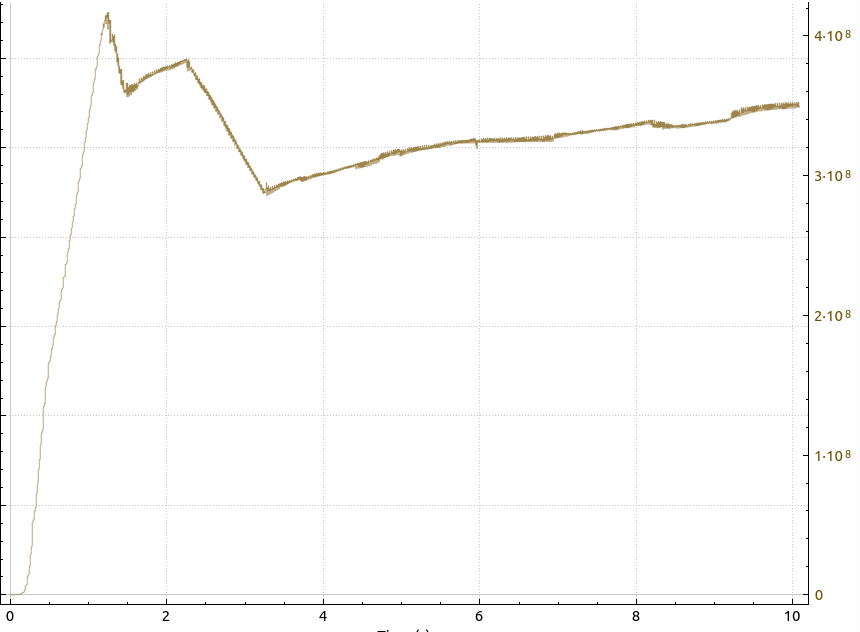
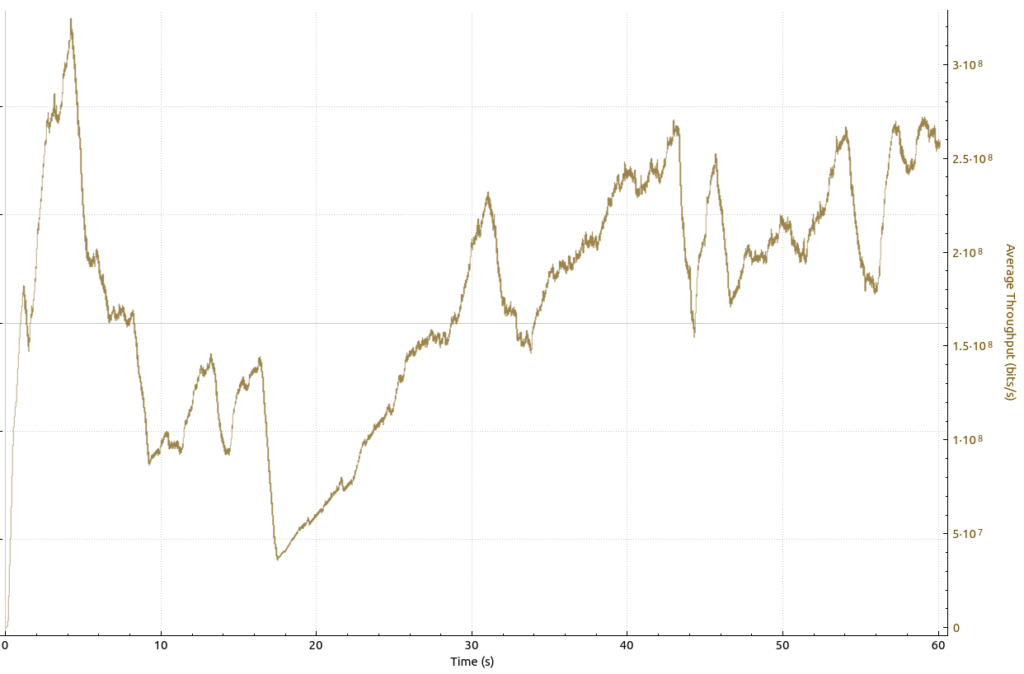
The favorite game of my teenage years was undoubtedly ‘Giana Sisters‘. I loved the game and the soundtrack and played it hours on end on my Commodore 64. A couple of decades then followed in which I didn’t play a lot of computer games at all, there were just so many other exciting things to do with computers that kept me engaged. Then, in 2012, Black Forrest Games had a Kickstarter campaign to create a modern successor to the game. I was hooked and once it was released, I bought it on Steam. Unfortunately, my 3 year old notebook I bought in 2009 would not run the game smoothly. I was a bit disappointed, but ok, it was not a gamer notebook. So I shelved the thing for a decade but was recently reminded of it again. So perhaps it would run now with my current media notebook with an Intel 11th generation CPU which still only has an integrated GPU? So lets see I thought…
Continue reading Steam – Giana Sisters – And Linux – 10 Years Later