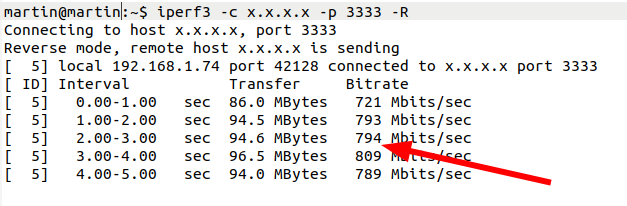
I’ve been traveling quite a bit by train in Germany lately and I take from the press that German network operators have made some effort to improve the on-train network experience. And indeed, the experience on a recent trip from Cologne to Hamburg was a lot better compared to what I remember from the past.
Continue reading On-Train Internet Experience between Cologne and Hamburg