In the previous post in my series on how to protect your privacy online I've looked at the TOR software which hides your location from prying eyes and encrypts all data right until the TOR exit node. I was delighted how easy it has become in recent years to install and use the package so the next logical step was to see how usable the Android variant of the package has become.
Installation of TOR on Android is straight forwarded. All that is required even on non-rooted devices is to install Orbot for the basic TOR functionality and Orweb, the web browser that uses Orbot. Both are available from app stores or can be installed directly from here and here.
 On non-rooted devices only the Orweb browser uses the TOR functionality provided by Orbot so all other applications continue to work as before and are obviously as unprotected as before. This can be both good and bad depending on the usage scenario. If TOR is only to be used for specific privacy sensitive web browsing sessions then this is the best setup as all security measures are automatically taken care of such as Java script being disabled, use of a generic browser ID when contacting web sites to prevent browser fingerprinting, no use of persistent cookies and no Flash. While this is perfect for privacy, such settings are likely to stand in the way for many everyday usage scenarios that are perhaps a bit less privacy sensitive. For these, the standard browser can be used as before as no settings are changed and Internet access is as direct as before.
On non-rooted devices only the Orweb browser uses the TOR functionality provided by Orbot so all other applications continue to work as before and are obviously as unprotected as before. This can be both good and bad depending on the usage scenario. If TOR is only to be used for specific privacy sensitive web browsing sessions then this is the best setup as all security measures are automatically taken care of such as Java script being disabled, use of a generic browser ID when contacting web sites to prevent browser fingerprinting, no use of persistent cookies and no Flash. While this is perfect for privacy, such settings are likely to stand in the way for many everyday usage scenarios that are perhaps a bit less privacy sensitive. For these, the standard browser can be used as before as no settings are changed and Internet access is as direct as before.
If Orbot is installed on a rooted Android device it can be used as an Internet proxy just like on the PC and all programs that are capable of standard proxy functionality can use a TOR tunnel. This way, mobile email, instant messaging and other applications can be protected as well.
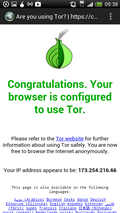 When starting Orweb, it offers the user to also start the Orbot background app if it hasn't been started before. After a couple of seconds the secure TOR tunnel is established and while using TOR has somewhat of a a speed impact I found it entirely usable. Unfortunately there are some usability restrictions introduced by the privacy model. There's no browsing history in the browser from which a previously visited website can be quickly reached and there are also no bookmarks. While I can understand both measures I think there should really be a bookmark feature even if it is a compromise, perhaps with a warning to the user that using bookmarks could reveal privacy sensitive information when the device is stolen. A solution to the problem could perhaps be bookmarks stored somewhere on the web anonymously and reachable via a short bit.ly link?
When starting Orweb, it offers the user to also start the Orbot background app if it hasn't been started before. After a couple of seconds the secure TOR tunnel is established and while using TOR has somewhat of a a speed impact I found it entirely usable. Unfortunately there are some usability restrictions introduced by the privacy model. There's no browsing history in the browser from which a previously visited website can be quickly reached and there are also no bookmarks. While I can understand both measures I think there should really be a bookmark feature even if it is a compromise, perhaps with a warning to the user that using bookmarks could reveal privacy sensitive information when the device is stolen. A solution to the problem could perhaps be bookmarks stored somewhere on the web anonymously and reachable via a short bit.ly link?
To sum up, I found TOR a great privacy protection tool for mobile use. It's easy to install and use but as on the PC, privacy and security means there are some usability limitations. I therefore prefer using TOR like on the PC in a two browser setup, one for my standard web browsing needs and another one for stuff where I would like to guard my privacy.