 Another outcome of my recent activities around SSL certificates and https encryption is that I've become aware that there are quite a number of different encryption algorithms a web server can choose from to secure a connection. These range from 'probably breakable instantly' by certain security agencies to pretty much unbreakable even if the key is compromised later on. So I've categorized the SSL encryption algorithms used today as follows:
Another outcome of my recent activities around SSL certificates and https encryption is that I've become aware that there are quite a number of different encryption algorithms a web server can choose from to secure a connection. These range from 'probably breakable instantly' by certain security agencies to pretty much unbreakable even if the key is compromised later on. So I've categorized the SSL encryption algorithms used today as follows:
Level 1 – breakable, should not be used anymore: This category contains encryption based on the RC4 stream cipher which is still used by quite a number of websites today including banks. This is surprising but many organizations felt that their use was a necessary evil because other algorithms were at some point prone to the so called BEAST attack.
Level 2: This category contains algorithms that do not use the RC4 stream cipher but which were unfortunately prone to the BEAST attack mentioned above. All browser manufacturers have reacted in the meantime and mitigated this sort of attack. One disadvantage of algorithms in this category is that data can be decrypted in real time or even later on if was recorded should an attacker be able to obtain of the private key.
Level 3: Perfect Forward Secrecy (PFS): Algorithms in this category use Diffie-Helman (DHE) or Elliptic Curve Diffie-Hellman key exchange (ECDHE) methods to negotiate session keys. This makes it impossible to decrypt recorded traffic should the private key be compromised in the future.
 Unfortunately web browsers do not indicate which algorithm is used to secure a https connection. Agreed, most people wouldn't know what to do with the information anyway but the same is true of the certificate details that can be viewed, e.g. in Firefox. So perhaps a feature for the future?
Unfortunately web browsers do not indicate which algorithm is used to secure a https connection. Agreed, most people wouldn't know what to do with the information anyway but the same is true of the certificate details that can be viewed, e.g. in Firefox. So perhaps a feature for the future?
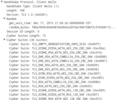
But while browsers are little help, Wireshark comes to the rescue. The first image on the left shows an excerpt of a 'Client Hello' message during the establishment of a HTTPS connection that gives the web server a list of all supported ciphering suites the browser supports. The list is actually quite long and cipher suites are ordered by preference. RC4 based cipher suits are pretty much at the bottom of the list and so far down they didn't even make it into the screenshot. The web server then selects one of the cipher suits and informs the web browser with a 'Sever Hello' message which one it has selected. This is shown in the second picture on the left. In this case an Elliptic Curve Diffie-Hellman cipher suite with perfect forward secrecy was selected. Excellent!
For further information I can recommend the SSL-Labs website. It offers an interesting SSL test for web sites and shows which ciphering suites are used when used with different browsers and gives lots of interesting background information (such as why RC4 should not be used anymore and why PFS is the way to go).