Last year I had a post that one has to be careful about establishing an IPv4-only VPN tunnel over a network interface that has a public IPv4 and a public IPv6 addresses assigned to it. If the DNS server on the other side of the VPN tunnel returns IPv6 addresses and the network stack on the client side prefers IPv6, which is usually the case, then the connection establishment will not go through the VPN tunnel but right around it via the physical network interface.
Quickly said at the time and quickly forgotten again as well as IPv6 connectivity is still rare these days. But those days are over as my mobile network operator of choice now supports IPv4v6 connectivity. When tethering my notebook via my smartphone now it configures itself for IPv4 and IPv6. That also means that I immediately get unwanted IPv6 leakage while using my VPN.
Some Mac and PC VPN client software used by some VPN providers seem to have built-in protection against it. On my Ubuntu systems, however, the OpenVPN client unfortunately does not. The only way to fix this on the client side is to disable IPv6 permanently or temporarily.
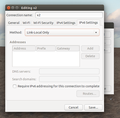 As I’d like to use IPv6 in general, I don’t want to disable it permanently. A temporary alternative for Ethernet and Wi-Fi connections is to to restrict IPv6 to link-local use as shown in the screenshot on the left. The problem is, however, that a new Wi-Fi connection that one creates e.g. at a hotel or exhibition venue will have full IPv6 enabled again and it’s more than likely that one forgets to turn it off manually after initial connection establishment.
As I’d like to use IPv6 in general, I don’t want to disable it permanently. A temporary alternative for Ethernet and Wi-Fi connections is to to restrict IPv6 to link-local use as shown in the screenshot on the left. The problem is, however, that a new Wi-Fi connection that one creates e.g. at a hotel or exhibition venue will have full IPv6 enabled again and it’s more than likely that one forgets to turn it off manually after initial connection establishment.
But why do DNS servers on the other side of an IPv4-only VPN actually have to return IPv6 addresses? I use Witopia for some scenarios and their DNS servers happily return IPv6 addresses. I wish they wouldn’t and it makes me wonder why they are doing it when their VPN service is limited to IPv4 anyway!?
Fortunately, I use my private VPN servers for most of my VPN needs. They also return IPv6 addresses but here I can change the behavior of the DNS servers behind the VPN server to only return IPv4 DNS results. As configuring that was a bit tricky I’ll make a separate blog post out of that. So stay tuned if you are interested!