 Back in December 2015 I found my first public Wifi network at 32C3 that used a certificate instead of a common password, not so much for user authentication but for assigning an individual ciphering key to each device. Especially at a hacker conference that’s a plus as normal WPA encryption uses the same passphrase for everyone and hence attackers can decrypt the Wifi traffic of others if they know the common passphrase and have intercepted the authentication dialog. When recently being asked to configure a computer for Eduroam access, an international Wifi network at universities (for a world map see here), I found yet another flavor of Wifi certificate use that is highly interesting.
Back in December 2015 I found my first public Wifi network at 32C3 that used a certificate instead of a common password, not so much for user authentication but for assigning an individual ciphering key to each device. Especially at a hacker conference that’s a plus as normal WPA encryption uses the same passphrase for everyone and hence attackers can decrypt the Wifi traffic of others if they know the common passphrase and have intercepted the authentication dialog. When recently being asked to configure a computer for Eduroam access, an international Wifi network at universities (for a world map see here), I found yet another flavor of Wifi certificate use that is highly interesting.
Authentication, Security, Encryption – The Basics
Unlike at the 32C3, certificates in Eduroam are not only used for authenticating the network towards the user but also to offer a secure way to authenticate a user towards the network. And finally the certificates are used in a way to allow the user to get access to the Internet at other universities around the world with his Eduroam setup without any reconfiguration on his side. So much for the theory let’s see how that works in practice:
Chain of Trust Between Universities
Apart from an individual username and password given to a student or university employee by his alma mater, a device needs to be configured with the public keys of the certificates used in the certificate chain of his particular university. To prevent man-in-the-middle attacks, the device needs to be further configured to only accept the certificate chain of this home university, even when he roams abroad.
All of these things are necessary so the device can check that the access point really belongs to the Eduroam network and was able to contact the authentication server of the user’s home university. This is required as the username/password combination is not transmitted in the clear between universities for security reasons. Instead, user credentials are always sent over a secure end-to-end tunnel to the home university. This way the visited university infrastructure never sees the user’s password in the clear. As all of these things are somewhat non-trivial to set-up on a device, Eduroam recommends using their installer program that puts all of these things in place.
The Eduroam Configuration Assistant Tool (CAT)
Fortunately, Eduroam not only serves the masses but also has an installer for Ubuntu that creates a new NetworkManager connection entry and copies all required certificates into a folder. As each university uses its own certificate chain and certificate name, a customized installer is required for each university. The customized installer also ensures that the certificate subject used by the home university is checked. In essence, 802.1x authentication of the network is configured in /etc/NetworkManager/system-connections/eduroam as follows:
[802-1x] eap=peap; identity=a8398493@univie.ac.at ca-cert=/home/..../eduroam-full-certificate-chain-university-of-vienna.pem # In Ubuntu up to 15.10 use the following line: subject-match=univie.ac.at # In Ubuntu 16.04 and newer use the following line: domain-suffix-match=univie.ac.at phase2-auth=mschapv2
Apart from the path to the certificate chain file the “subject-match” or “dommain-suffix-match” line (depending on the Ubuntu version) are equally important so the device rejects any certificate chain not belonging to the home university of the user. In combination this prevents man-in-the-middle attacks. For further details have a look here.
Protecting Privacy with an Anonymous Identity – Will Break Roaming Though…
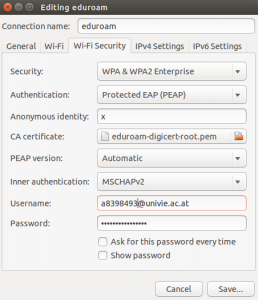 To protect a user’s privacy one could put a random value into the “Anonymous identity” field in the NetworkManager entry for Eduroam. Otherwise the username is transmitted in the clear during the initial session establishment. This is not a security issue but it somewhat degrades privacy. The screenshot on the left shows my Eduroam configuration on Ubuntu with an “x” in the “Anonymous identity” field to prevent privacy leakage. If left empty the real user name “a8398493@univie.ac.at” would be transmitted in the clear. Obviously it would be even better if Ubuntu’s NetworkManager could be configured to send a different value each time it connects but there doesn’t seem to be such an option. Note that using a random “Anonymous identity” will break roaming capabilities as the field is used at another university to find the home university of the user (for details see section 6.2 here). This can be fixed by using a random identity while leaving the realm (@univie.ac.at) in place so the routing of the request to the home university works correctly.
To protect a user’s privacy one could put a random value into the “Anonymous identity” field in the NetworkManager entry for Eduroam. Otherwise the username is transmitted in the clear during the initial session establishment. This is not a security issue but it somewhat degrades privacy. The screenshot on the left shows my Eduroam configuration on Ubuntu with an “x” in the “Anonymous identity” field to prevent privacy leakage. If left empty the real user name “a8398493@univie.ac.at” would be transmitted in the clear. Obviously it would be even better if Ubuntu’s NetworkManager could be configured to send a different value each time it connects but there doesn’t seem to be such an option. Note that using a random “Anonymous identity” will break roaming capabilities as the field is used at another university to find the home university of the user (for details see section 6.2 here). This can be fixed by using a random identity while leaving the realm (@univie.ac.at) in place so the routing of the request to the home university works correctly.
An important note: If the Eduroam connection profile is changed via the NetworkManager GUI, the subject-match or dommain-suffix-match line, which is vital to prevent man-in-the-middle attacks, is unfortunately removed and has to be added manually again by editing the file!
PEAP vs. TTLS
While it would be desirable to have a single method to use a certificate to authenticate the server and a user name and password to authenticate a user, several exist in practice. While at 32C3, TTLS was used, Eduroam uses PEAP. Not a big issue but the configuration dialog looks a bit different depending on which method is used. The screenshot on the left shows the PEAP configuration for Eduroam while this screenshot shows the 32C3 TTLS setup.
Public IPv4 and IPv6 Addresses at the University of Vienna
While authentication and access authorization is always negotiated with the radius server at the home university over an encrypted end-to-end tunnel (see here fore details), IP connectivity is provided locally. In the building at the University of Vienna I set up a computer, connectivity was really fast, both uplink and downlink speed easily eclipsed 10 Mbit/s. I was even more surprised to see that the device was assigned a public IPv4 and also a public IPv6 addresses. No Network Address Translation and no filtering of incoming IPv6 session establishment packets. Pinging from a remote host to the device in the Eduroam network in Vienna worked just as well as incoming TCP SYN packets for ssh, telnet and ftp. Great, that’s how connectivity should be, peer to peer!
Update 3.5.2016: Ubuntu 16.04 requires a new parameter to properly check the certificate.