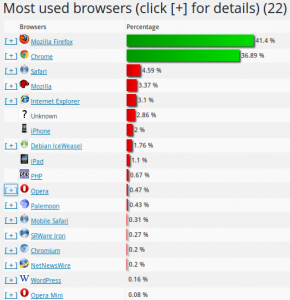
When Thalys started to offer Wifi service in 2009 on their trains in Europe I was ecstatic as it was working great. Over the years however, their service deteriorated to something barely usable (see here, here and here) and has remained so ever since. In contrast to their service, Internet access on high speed trains in Germany has remained mostly usable over the years. Instead of satellites, Deutsche Bahn (DB) has been using a dedicated cellular network along the railway lines and has upgraded to UMTS and LTE over the years to increase capacity. So far, the service was not free so the number of users was limited and the network has remained usable. Now, however, driven by national politics who is looking for quick and simple answers, DB needs to upgrade the system and offer it for free to all passengers. A recipe for disaster?
Continue reading I Like Free Wifi on The Train – But Would I rather want to Pay for it?