It’s become almost a tradition for me in December each year to have a look back at what happened in the previous 12 months in the telecoms industry and in my private technology endeavors that have left long lasting impression or have marked the start of something new. And so here we go again, in the 10th year of this blog’s existence. Yes, it has already been a decade, time passes quickly!
First lets have a look at the telecoms sector. Early in 2015, 3GPP announced that they have embarked on their voyage to 5G and have published a time table that shows what they intend to do right into the 2020s. Everybody is talking about it but nobody seems to know what it really is. NGNM has published a whitpaper containing use cases and 3GPP now looks how specifications can be enhanced and newly created to fulfill those visions. I had quite a number of posts on various aspects of 5G, such as thinking about what 5G is in the first place, debunking the 1 ms 5G myth and two looks at the use of super high frequencies beyond 5 GHz, stating that such frequency bands are only usable for transmitting data over very short distances and an opposite statement made in a very interesting IEEE paper.
On the other end of the spectrum, GSM networks are starting to be switched-off and many announcing a switch-off in the years to come. 3G also has limited lifetime left with some network operators thinking about a 2020 switch-off date. Personally, I can’t wait for GSM to be switched-off.
In recent years we have seen quite a number of network operators merging in different parts of Europe, thus reducing competition which made me wonder if Free in France will keep the title as last launched 4th network operator in Europe forever. There are certainly no signs they are going to lose that tile anytime soon.
Speaking of evolution I had a look back of how mobiles looked like a couple of years ago to show what has changed in mobile computing in the last 5 years and how that compares to the (few) changes in the desktop computer industry. Quite a contrast. And speaking of change, we are now officially past peak telephony in many countries in Europe including Germany when fixed line and mobile phone minutes are combined.
Over the clouds we haven’t peaked anywhere yet when it comes to connectivity. I had a number of positive ‘over the cloud’ connectivity experiences this year but with LTE ground to air it is likely to be topped in the future.
Back on earth with wires attached, I’ve been migrated from VDSL+ISDN at home to an all-IP connection with fixed line VoIP. Not that it had been my free will but I got quite a number of advantages from the move, including an upgrade from 25 to 50 Mbit/s in the downlink direction, from 5 to 10 Mbit/s in the uplink direction and HD-voice speech quality between fixed line and mobile.
Staying for a moment longer in the voice call domain, despite moving past peak telephony, I was really glad to get rid of Skype on the PC and to put it on a tablet where this proprietary piece of software will hopefully do less harm. On the other hand, I learned to like Skype while traveling to Asia as Skype over LTE is significantly cheaper than circuit switched voice for me while voice quality is significantly better. Not that I would install it on my mobile device that contains my private data but I rarely travel with only a single mobile device.
On the hardware side there have been a number of really important projects for my private development this year. The most important one, no doubt, has been the 4-Bit Nibbler CPU project about which I had many blog entries and on which I spend many weeks to put it together and finally realizing my dream understanding how computers really work by actually building a CPU from several chips.
On a more global scale, I was rocked by the announcement of the Raspberry Pi Zero, the first fully working computer that has been shipped as a magazine complement. This is a milestone in computing history not only for being small and cheap enough to fit onto the cover of a computer magazine. If you’ve lived under a stone for the past few months and haven’t heard of it, this is the story to check out!
When it comes to vintage computing, 2015 has also been an interesting year for me in that area, too. I’m a proud owner again of a Commodore C64 and an Amiga 500 and disk drives that take today’s SD cards instead of real 5.25 or 3.5 floppy disks have greatly helped me to explore my personal computing history and home computing history in general. The culmination in my vintage adventure has certainly been the 30th anniversary celebration of the Amiga in Neuss, Germany and the many people I met there with a similar passion for the home computers that had a significant impact on them when they were teenagers.
Before I get too nostalgic let’s better get back to 2015. My software discovery of the year has certainly been ‘Conversations’ an open source XMPP client app for Android that looks and feels very much like Whatsapp but offers privacy and confidentiality without compromising usability. I’m using it for about half a year now and in the meantime I’ve been able to convince quite a number of my friends that this is the way to communicate not only with me but also with their friends. Further on the software side, the Selfoss RSS reader continues to be an important tool I user several times a day to keep up to date with what is going on in the world. As it’s open source, I contributed some code for it as part of keeping myself current with PHP and database programming.
And last, but not least, I’ve read a couple of great books about computing this year, especially to better understand computing history and the history of free and open source software. ‘The Innovators‘ and ‘Fire in the Valley‘ comes to mind as well as ‘Rebel Code‘, ‘Commodore – A Company on the Edge’, ‘Amiga – The Future was here’ and ‘Diary of an 80s Computer Geek‘. And on the fiction side, I very much enjoyed ‘Chronos‘ and ‘The Martian‘, both excellent reads. As far as ‘The Martian’ is concerned, there’s a movie based on the book now, which I haven’t seen because in my opinion there’s no way it can be even half as good as the book has been. So if you haven’t seen it either, my advice is not to go for the DVD but to read the book.
There we go, this has been 2015 for me on the technology side. What a great year!
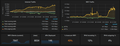 12.000 people have bought tickets for the 32C3 and while they consumer a lot of data from the Internet it's easily dwarfed by the amount of data that is flowing from the congress to the outside world. How much of that are the live and recorded video streams is hard to tell but I guess it might be a fair amount. The screenshot on the left shows the state of affairs at 6 pm on day 2 of the congress:
12.000 people have bought tickets for the 32C3 and while they consumer a lot of data from the Internet it's easily dwarfed by the amount of data that is flowing from the congress to the outside world. How much of that are the live and recorded video streams is hard to tell but I guess it might be a fair amount. The screenshot on the left shows the state of affairs at 6 pm on day 2 of the congress: