 In a previous post I wrote about what has changed in desktop computing in the last 6 years. In summary not very much, I still use my notebook from back then for some purposes with an up to date operating system for multimedia consumption. So what about mobile computing and mobile devices, how have things evolved in this domain in the same time frame?
In a previous post I wrote about what has changed in desktop computing in the last 6 years. In summary not very much, I still use my notebook from back then for some purposes with an up to date operating system for multimedia consumption. So what about mobile computing and mobile devices, how have things evolved in this domain in the same time frame?
Back in 2008 I wrote a review of how well an entry level phone at the time, a Nokia 5000, could be used for email and web browsing. Back then, the point was to show that even with an entry level device, it had become possible to surf the web and use the device for email communication. It was a sensation. So let's have a look at how the 7 year old Nokia 5000 compares to a similar device that can be bought today.
Price
For my comparison I chose the Android based LG D160, released back in 2014 and which is currently available for around 56 euros, contract free, VAT included. That is only around 60% of the price I paid for the Nokia 5000 at the time, which cost 90 euros. I could have made a comparison to a device that also costs 90 euros today but I wanted to compare two entry level devices and the cost of such a device has come down significantly over the years.
Connectivity
At the time, being able to browse the web with an entry level device was spectacular, today it's a given, nobody would think otherwise anymore. Back then I used Opera Mini with a compression server in the cloud to reduce the size and complexity of the web page. This was necessary on the one hand because the Nokia 5000 only came with a 2G EDGE network interface that could at best transport around 250 kbit of data per second. 3G networks did exist at the time and already covered bigger cities, but entry level devices were still limited to 2G networks. Compression was also necessary due to the processing power and memory having been quite low on the Nokia 5000 compared to today's devices. The LG D160 of 2014 on the other hand comes equipped with a 3G HSPA network interface with data transfer speeds of up to 14.4 Mbit/s. LTE networks are available nationwide today but it's the same story as with 3G for the Nokia 5000 then, LTE hasn't moved down into entry level category yet. What is included today that was considered a high end feature at the time is Wi-Fi, so the device can be used at home without a cellular network. Also, the device supports tethering, so it can be used as a gateway to the Internet for a notebook or tablet on the move.
Screen and Web Browsing
The image on the left shows the Nokia 5000 and the LG D160 side by side and next to a Samsung Galaxy S4, a flagship device back in 2013. While the Nokia 5000 back in 2008 came with a 320×240 pixel screen capable of 65k colors, the LG D160 now has a 320×480 pixel screen with 16 million colors. By today's standards that is a very low resolution but compared to 2008 it is still twice the number of pixels. Opera is still my browser of choice but I have moved-on from Opera Mini to Opera, a full web browser that no longer requires a compression server on the backend as the device has enough RAM and processing power to show mobile optimized and even full web pages without any magic applied in between. At the time it took around 12 seconds to launch the browser and there was no multitasking. Still acceptable then but today, the browser launches in 4 seconds and even stays in memory if no other big apps are running despite the 512 MB RAM, which is a massive amount compared to 2009, but rather little today. GSMArena doesn't even specify how much RAM was built into the Nokia 5000 but the 12 MB of Flash memory for file storage compared to the 4 GB in the D160 today are a pretty good indication of what it must have been. Another aspect I focused on at the time was how fast and smooth scrolling and I noted that compared to the flagship Nokia N95 at the time it was slower and not as smooth. Still usable was the verdict. Today, scrolling of normal web pages via a touchscreen is quite smooth on the D160 and light-years away from what was possible on entry level devices in 2008/9.
eMail
At the time, the email client in the Nokia 5000 was quite rudimentary, with important options such as partial downloads missing. Also, there were few if any email apps for non-smartphone devices at the time to improve the situation. Today, even the 40% cheaper D160 easily runs sophisticated email clients such as K9 mail that, apart from a proper PGP implementation, leaves little to be desired.
Camera, Navigation and Apps
When it comes to built-in cameras, the Nokia 5000 from back in 2009 has a 1 MP camera at the back while today's D160 has a 3 MP camera built in. Both take pictures but they would both be rated pretty much worthless by the standards of each period. But still, the camera is significantly better at a much reduced price compared to 2009. One big advantage of today's entry level smartphones compared to 2009 is the built in GPS chip for a variety of uses from finding the closest Italian restaurant to car navigation. I didn't install Osmand on the D160 but Google maps pinpointed my location in seconds and presented me with a route to a destination almost instantly. An incredible improvement over the state of the art in 2009 in this price category. I mentioned the price tag on purpose as Nokia Maps with car navigation existed in 2008/9 (see here and here) but could only be used on much more expensive Symbian OS based devices. And a final point to make in this review is the availability of apps now and then. Few apps and games existed for entry level devices back then. Today, even the very low cost D160 can handle most Android apps and many if not most games (I'm no expert when it comes to gaming). Also, SMS messaging is quickly dissapearing with most people not caring about privacy and using Internet based multimedia replacement solutions such as WhatsApp instead.
Summary
So while I still use the notebook I bought back in 2009 with the latest operating system version on the market today, the entry level phone from back then is so outdated by today's entry level state of the art that I find quite shocking. Incredible how things have advanced in mobile in this short amount of time.
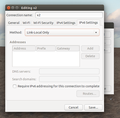 As I’d like to use IPv6 in general, I don’t want to disable it permanently. A temporary alternative for Ethernet and Wi-Fi connections is to to restrict IPv6 to link-local use as shown in the screenshot on the left. The problem is, however, that a new Wi-Fi connection that one creates e.g. at a hotel or exhibition venue will have full IPv6 enabled again and it’s more than likely that one forgets to turn it off manually after initial connection establishment.
As I’d like to use IPv6 in general, I don’t want to disable it permanently. A temporary alternative for Ethernet and Wi-Fi connections is to to restrict IPv6 to link-local use as shown in the screenshot on the left. The problem is, however, that a new Wi-Fi connection that one creates e.g. at a hotel or exhibition venue will have full IPv6 enabled again and it’s more than likely that one forgets to turn it off manually after initial connection establishment.