About one and a half years ago I first reported about Nokia R&D Labs great idea to port parts of the Apache Server code over to the S60 OS mobile phone platform. The web server in your pocket, a strange idea maybe at first but with a lot of potential. At the time I mused in this blog post how I would use it in my daily live. Now, Nokia has released the project to the public and created a single installation file that contains everything. Thank you Tommy for posting it on your blog!
 It seems that what I was writing about previously and much much more has found it’s way into the first version. As described before, a mobile web server can be used for sharing content created or stored on the phone with other people. The owner of the phone also benefits from the web server himself as he can use a web browser on a PC to quickly and comfortably access the mobile phone via the web browser to search for a name in the contact list, to look at his calendar, to create new meeting entries, to send SMS messages, etc. etc.
It seems that what I was writing about previously and much much more has found it’s way into the first version. As described before, a mobile web server can be used for sharing content created or stored on the phone with other people. The owner of the phone also benefits from the web server himself as he can use a web browser on a PC to quickly and comfortably access the mobile phone via the web browser to search for a name in the contact list, to look at his calendar, to create new meeting entries, to send SMS messages, etc. etc.
Of course I had to immediately install the web server on my N93 and give it a try myself.
How To Access The Web Server
Via the Internet: After registration on Nokia’s Mobile Web Server Site and installation of the mobile web server (a single .sis file) on the mobile phone, the web server can be connected to the Internet. If connected via a cellular network, the owner or other people can use the URL assigned during the registration process (e.g. martin.mymobilesite.net) to access the phone.
It’s important to note that the URL is not directly registered to the IP address of the mobile phone but instead leads to the Nokia project site which forwards the request. This is necessary as many mobile operators do not give out public IP addresses and thus computers on the Internet can not reach the mobile phone directly. The Nokia project site, however, is contacted by the mobile web server at startup and thus has an open TCP connection that can be used for forwarding the request.
Via Wifi: Many N-series phones can be connected to the Internet via Wifi. This has the advantage that the owner can not only contact the phone via the Nokia project server but directly with a notebook or PC connected to the same Wifi network. This has the advantage that pages are sent much faster as the data is not sent once to the Internet and back.
Applications
A web server is nothing without static and dynamic pages it can supply to web browsers. Thus, the mobile web server already comes with a number of server side applications and access to each application can be permitted or denied per user or per group. Here are my favorites:
Camera Application: Permitted users can invoke a server side application that takes a picture with the phone’s camera which is then returned to the web browser. An excellent way for home monitoring purposes!
Share Photo Albums: Pictures stored on the phone can be assigned to photo albums which users can access once the owner of the phone gives them access. Very nice, one photo album from my friends, one for my parents, one for business partners, etc. etc.
Contact List Browser: Instead of searching for a contact on the mobile phone, permitted users can search addresses and phone numbers stored on the phone. This is probably an application that the owner wants to restrict to himself. By default all applications are restricted to the owner and thus access to any sensitive information is not given out by default. Excellent default security policy!
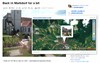
Calendar Application: The phone’s calender can be viewed and new calender entries can be created in the web browser. The picture at the beginning of the blog entry shows how the application presents the calendar entries for a week.
Send SMS messages: Gone are the days of fiddling around with the keys on the phone when writing an SMS. Now, the SMS can be written in the web browser no matter if the phone is next to the notebook or 5000km away.
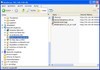
WebDAV: I like to use my phones as a storage device to take files with me or to make a quick backup. So far I always had to connect the phone to the notebook with a cable or establish a Bluetooth connection to transfer the files. With WebDAV the phone can now seamlessly share files and folders with a PC. The picture on the left shows how the file system of the phone is integrated into the PC’s file explorer tree structure. Files can be copied to and from the WebDAV drive, renamed and deleted. As with all other server side applications the owner of the phone can assign access rights to individual users. For Windows XP no additional software is necessary. When connected via Wifi, file transfers to the phone are done with a speed of about 50 kbytes/s. Transferring a file from the phone to the PC is almost done at light speed, I measured around 600 kbytes/s.
Create your own applications: The mobile web server is open for additional server side modules and a Python interpreter is also included. Want to query an external GPS receiver to create a page that shows your current location? No problem, Python can do the trick and only a text editor is required to write the code. Fabulous. More information can be found here.
Battery Usage
Surprisingly, battery usage while connected via Wifi does not seem to be very high. I’ve had the phone connected for 5-6 hours today and the battery indicator only decreased by two bars. Needless to say I also used the phone during the day for a lot of other things so the web server and the Wifi chip where not the only ones using the battery sucking on the battery.
Summary
I am absolutely thrilled to see such a complete suite of applications to be delivered with the first version of the server. Also, the user management is superb as it allows to give access rights for each application to individual user or per groups Thus, the owner can restrict applications like the calendar, SMS sending and the contacts to himself while sharing photo albums and grant access to take snapshots with the camera to selected other users. Overall, I think this is a project that will surely generate interest and hopefully a lot of interesting user supplied modules and Python scripts.