While in Europe, GSM, UMTS and LTE are used by all network operators, the US wireless landscape has always been much more diverse. This meant and still means that there always had and have to be several device variants to support different networks. But with the advent of LTE and advances in chip technology this may be about to change.
When Google recently introduced the 2013 version of the Nexus 7 tablet, it upgraded the cellular hardware to support 7 LTE bands. For details see Google's page on the Nexus 7 and AnandTech's mini review over here which has a somewhat different frequency listing. Apart from the stunning number of supported LTE bands it also supports the five major UMTS frequency bands.
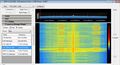
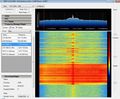
The LTE band combination for the US is especially interesting, as band 13 is included for Verizon's LTE, band 17 for AT&T's LTE and band 4 for T-Mobile's LTE. This might very well become the future trend and will finally allow US consumers the same flexibility as in Europe to buy a device independent of the network operator or even change network operators over the life cycle of the device.
I'm not quite sure how Sprint fits into this equation!? From what I can tell they have LTE up and running in a 1900 MHz band and have taken over Clearwire's 2500 MHz TDD assets. While the 2500 MHz TDD band is not supported by the device I have no information which band Sprint uses with it's 1900 MHz assets. If you have some more information on that, please leave a comment.
Also interesting is the absence of CDMA support in the tablet. Probably not surprising for a tablet, as mobile telephony, if implemented on the user interface at all, is not a prime use case for a tablet. Also, unlike UMTS with it's great data rates, CDMA EvDo only offers limited speeds which are undesirable in a data heavy product as well. So why bother?