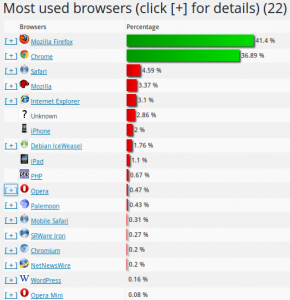
After recently upgrading my VDSL line at home, it was also time to upgrade my Wi-Fi equipment to support the higher speeds. When doing some speed tests after the upgrade I noticed to my satisfaction that my Wi-Fi connectivity now easily supports the 50 MBit/s VDSL line. I also noticed, however that downloading a file from a local web server at 100 MBit/s takes a heavy toll on my CPU, it’s almost completely maxed out. At first I suspected the Wi-Fi driver to cause the high load but I soon found out that Firefox is the actual culprit.
Continue reading Forget About Using Firefox When Testing Network Throughput