 For ordinary files, the write speed of USB Flash sticks is probably of only secondary importance. However, when writing large files onto them, for example ISO images of Linux distributions or virtual machine images, write speed becomes an important factor.
For ordinary files, the write speed of USB Flash sticks is probably of only secondary importance. However, when writing large files onto them, for example ISO images of Linux distributions or virtual machine images, write speed becomes an important factor.
Writing a 1 GB file to a slow USB flash disk at 1 Mbyte/s takes over 16 minutes while the same operation takes just over a minute when using a fast USB Flash disk that can write around 12 Mbyte/s to its Flash cells. And that's about the span I discovered on my various USB flash disks that have accumulated over the years. I have a couple of physically very small 4 GB USB sticks that hardly stick out from a USB port but the 1 Mbyte/s write speed is just measly. It's probably not due to their size as similar sized current models are advertised with write speeds of around 5-6 Mbyte/s.
Then I have a number of USB sticks with capacities between 2 GB and 16 GB of various sizes. Most of them are capable to write between 4.5 and 6.5 Mbyte/s to their flash cells. But that's still slow for 1+ GB sized files so I ordered a couple of 8 GB Transcend Ultra Speed USB sticks as they are rated for writing speeds of 12 Mbyte/s. And indeed, when testing them I could get 12.5 Mbyte/s of sustained writing speed out of them on sequential large file writes. Random write access is a bit slower, around 4.5 Mbyte/s.
When reading data on the sticks I see data rates between 20 Mbyte/s on the slowest ones up to 35 Mbyte/s on the Transcend Ultra Speed, which is pretty much the limit of the USB 2 port. Perhaps I should also try a USB 3 capable Flash stick. I don't have a USB 3 port on my PC but the write speed of these sticks seem to be again much faster.
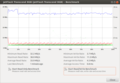
The picture on the left shows the read and write speeds of the Transcend stick. The average write rate seems to be from random writes as writing a 1 GB file to resulted in a write rate of 12.5 Mbyte/s (timed with a watch, with unmount afterwards to ensure empty buffers).