Both WiMAX and the UMTS successor technology LTE use Orthogonal Frequency Division Multiplexing (OFDM) as the core modulation technology on the air interface in downlink direction. In uplink direction, however, the two systems go different ways. While WiMAX uses OFDMA (Orthogonal Frequency Division Multiple Access), the 3GPP (3rd Generation Partnership Project) standardization group has decided to use SC-FDMA (Single Carrier Frequency Division Multiple Access) instead.
In essence, SC-FDMA builds on OFDMA so the two systems are not as different as it seems at first. In addition, the abbreviation SC-FDMA is quite misleading as the technology, like OFDMA, also uses many sub-carriers on the air interface. To explain how SC-FDMA works it’s best to first take a look at OFDMA (used by WiMAX) and then discuss the differences to SC-FDMA.
OFDMA
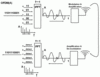
OFDMA transmits a data stream by using several narrow band sub-carriers simultaneously, e.g. 512, 1024 or even more depending on the overall available bandwidth (e.g. 5, 10, 20 MHz) of the channel. As many bits are transported in parallel, the transmission speed on each sub carrier can be much lower than the overall resulting data rate. This is important in a practical radio environment in order to minimize effect of multipath fading created by slightly different arrival times of the signal from different directions.
As shown in the first figure on the left the input bits are first grouped and assigned for transmission over different frequencies (sub-carriers). In the example, 4 bits (representing a 16QAM modulation) are using for constructing each sub-carrier. In theory, each sub-carrier signal could be generated by a separate transmission chain hardware block. The output of these blocks would then have to be summed up and the resulting signal could then be sent over the air. Due to the high number of sub-carriers used this approach is not practicable. Instead, a mathematical approach is taken: As each sub-carrier is transmitted on a different frequency a graph which shows the frequency on the x-axis and the amplitude of each sub-carrier on the y-axis can be constructed. Then, a mathematical functional called Inverse Fast Fourier Transformation (IFFT) is applied which transforms the diagram from the frequency domain to time domain. This diagram has the time on the x-axis and represents the same signal as would have been generated by the separate transmission chains for each sub-carrier when summed up. The IFFT thus does exactly the same as the separate transmission chains for each sub carrier would do including summing up the individual results.
On the receiver side the signal is first demodulated and amplified. The result is then treated by a Fast Fourier Transformation function which converts the time signal back into the frequency domain. This reconstructs the frequency/amplitude diagram created at the transmitter. At the center frequency of each sub-carrier a detector function is then used to generate the bits which were originally used to create the sub-carrier.
SC-FDMA
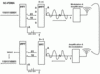
Despite its name, Single Carrier Frequency Division Multiple Access (SC-FDMA) also transmits data over the air interface in many sub-carriers but adds an additional processing step as shown in the second figure. Instead of putting 4 bits together as in the OFDM example to form the signal for one sub-carrier, the additional processing block in SC-FDMA spreads the information of each bit over all the sub-carriers. This is done as follows: Again, a number of bits (e.g. 4 representing a 16 QAM modulation) are grouped together. In OFDM, these groups of bits would have been the input of the IDFT. In SC-FDMA, however, these bits are now piped into a Fast Fourier Transformation (FFT) function first. The output of the process is the basis for the creation of the sub-carriers for the following IFFT. As not all sub-carriers are used by the mobile station, many of them are set to zero in the diagram. These may or may not be used by other mobile stations.
On the receiver side the signal is demodulated, amplified and treated by the Fast Fourier Transformation function in the same way as in OFDMA. The resulting amplitude diagram, however, is now not analyzed straight away to get the original data stream but fed to the Inverse Fast Fourier Transformation function to remove the effect of the additional signal processing originally done at the transmitter side. The result of the IFFT is again a time domain signal. The time domain signal is now fed to a single detector block which recreates the original bits. Thus, instead of detecting the bits on many different sub-carriers, only a single detector is used on a single carrier.
Summary of the difference between OFDM and SC-FDMA:
OFDM takes groups of input bits (0’s and 1’s) to assemble the sub-carriers which are then processed by the IDFT to get a time signal. SC-FDMA in contrast first runs an FFT over the groups of input bits to spread them over all sub-carriers and then uses the result for the IDFT which creates the time signal. This is why SC-FDMA is sometimes also referred to as FFT spread OFDM.
While SC-FDMA adds additional complexity at both the transmitter and receiver side, the 3GPP standardization body has nevertheless decided for it as treating signal this way reduces the Peak to Average Power Ratio (PAPR). This is important to lower the power consumption of mobile devices. More details on PAPR can be found here.

