![]() I use OpenVPN every day on the move for a number of purposes. Especially in open WiFi environments in hotels and other places it ensures that my data can’t be easily intercepted over the unencrypted WiFi interface. In most situations, however, setting up a VPN tunnel is only a temporary measure, usually for a couple of hours at most. As a consequence I didn’t really have a feeling for how stable an OpenVPN connection is over the long run. Up until now that is.
I use OpenVPN every day on the move for a number of purposes. Especially in open WiFi environments in hotels and other places it ensures that my data can’t be easily intercepted over the unencrypted WiFi interface. In most situations, however, setting up a VPN tunnel is only a temporary measure, usually for a couple of hours at most. As a consequence I didn’t really have a feeling for how stable an OpenVPN connection is over the long run. Up until now that is.
Author: Martin
A Quick eCall Overview
Some things are so glacially slow that you almost don’t see them coming until they are there. eCall is probably such a thing and here’s a quick overview in case you go back to sleep again on the topic and need to refresh your memory quickly when it comes up again in a couple of years.
Keeping My Emergency Spare Backup Drive Up To Date In A Jiffy
In a previous post on the topic I’ve talked about the part of my backup strategy to keep an emergency spare hard drive up to date by copying data that has changed from a backup drive to it every now and then. This way I have a 1:1 copy of my system partition and all of my data at any time. A slight downside of this scheme is that in addition to a spare notebook and the emergency backup drive, I would have to take a backup drive with me when I travel to be prepared in case the unthinkable happens. After thinking about it a bit further I’ve now come up with a way to copy modified data directly from my notebook to the spare backup drive without the need for a separate backup disk in between.
Continue reading Keeping My Emergency Spare Backup Drive Up To Date In A Jiffy
RAN Sharing – MOCN and MORAN
In a previous post I’ve been talking about the high number of UMTS and LTE networks I’ve been observing in Bangalore and that I had did not see the kind of network sharing in my traces that I was expecting. I didn’t go into the details of the different kinds of network sharing in this post so I’ll follow up with the details here.
UK To Become First Country With A 4G Public Safety Network That Uses A Commercial Network?
When I wrote my 3 part overview of LTE-A Pro for Public Safety Services back in January this year I wasn’t aware that just a couple of weeks earlier the UK government has given out a contract to build a 4G Public Safety Services network that, from what I read between the lines, will be piggybacked onto EE’s (soon BT’s) commercial LTE network.
2nd Hand Computing
Ever thought about buying a 2nd-hand notebook? Me neither until recently when a friend asked for advice. At first I was quite skeptical but it turns out it’s an interesting option and in the meantime I even bought one for myself.
IPv6 When Tethering
Just because a smartphone can get an IPv6 address from a cellular network doesn’t necessarily mean that its tethering functionality is also IPv6 capable. Fortunately, I’ve noticed in practice that more and more devices that are coming to the market these days have implemented the feature. And here is how it works:
Making A Good Backup Strategy Even Better – Instant Usability
 Over the years, my backup strategy with Clonezilla and Lucky Backup have helped me quite a number of times, especially back in January when a notebook under my care was stolen while traveling. With my backup strategy it takes around 30 minutes to restore an image of the system partition on an emergency spare hard drive and a couple of hours to restore the data partition with half a terabyte of data. While I would say that such times are more than acceptable I was not quite happy about the time it takes to restore the data and have now found a simple solution to restore the data partition in just a few minutes as well.
Over the years, my backup strategy with Clonezilla and Lucky Backup have helped me quite a number of times, especially back in January when a notebook under my care was stolen while traveling. With my backup strategy it takes around 30 minutes to restore an image of the system partition on an emergency spare hard drive and a couple of hours to restore the data partition with half a terabyte of data. While I would say that such times are more than acceptable I was not quite happy about the time it takes to restore the data and have now found a simple solution to restore the data partition in just a few minutes as well.
Continue reading Making A Good Backup Strategy Even Better – Instant Usability
Amazon Prime Video Now Usable On Linux, Too!
DRM protected content is a hotly debated topic and not without side effects but I have to admit I was somewhat glad when Netflix added support for Chrome and HTML5 playback on Linux back in 2014. At the time I also experimented with Amazon Prime video which was using Flash. Unfortunately this solution was quite unstable and thus unusable. Recently I noticed, however, that Amazon now also supports Chrome and HTML5 video playback on Linux. Over the past weeks I’ve watched a few full length movies and playback is now flawless. Well done, Amazon, thanks! … Just remove that DRM now please…
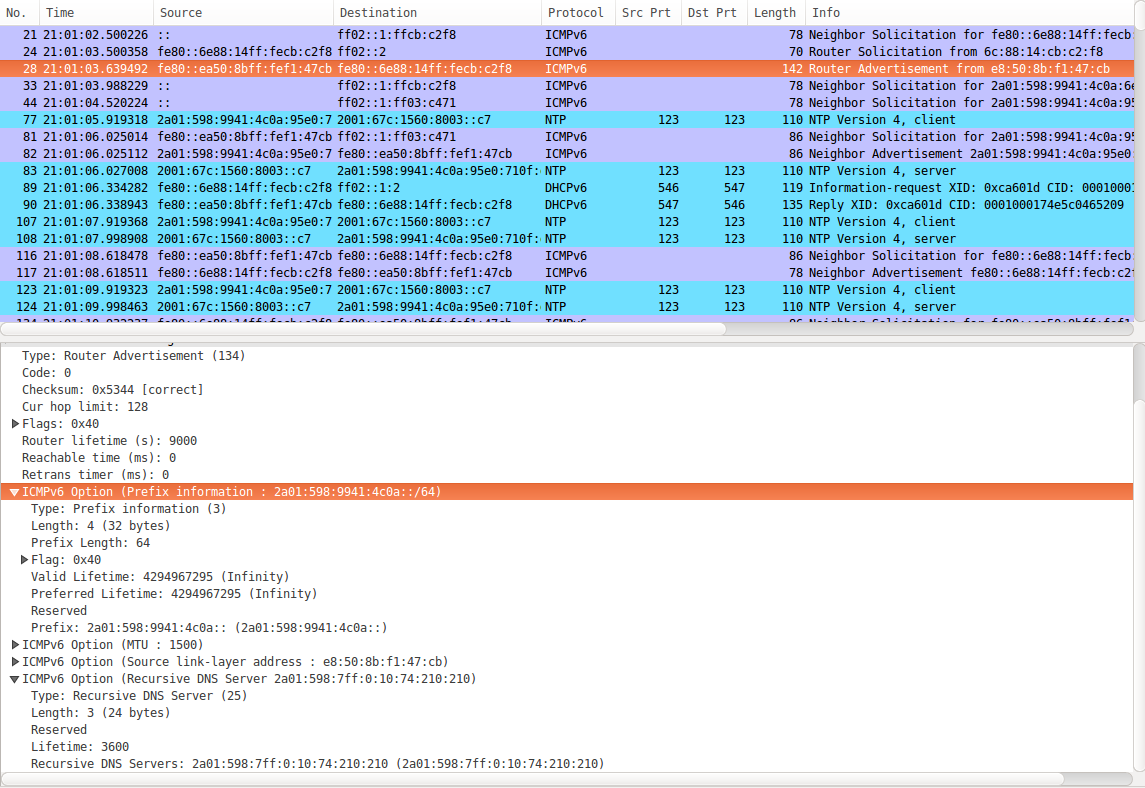
IPv6 When Roaming – Part 2
A couple of weeks ago I had a post in which I noted that while I have mobile IPv4v6 connectivity while I’m in my home country, I get IPv4-only connectivity when roaming by default. Now it looks like this is not universally true anymore.