Two and a half years ago in March 2015 I had my first post on 5G on this site about 3GPP kicking off its 5G activities. A lot has happened since then and I had the occasional post but now things are getting really exciting for me: Various 3GPP groups have started churning out the first drafts of Technical Specifications (TS) rather than refining the many different implementation options discussed in many different 3GPP Technical Reports (TR). In other words the technical specifications are now written based on the agreed-on options from the TRs. So now is the time to have a first look what is going to be put into practice.
Category: Uncategorized
Like the GPU, WiFi Now Moves Into The Intel CPU
Once upon a time a CPU in a notebook was just the central processing unit and all other functionality like memory controler, graphics, high speed buses, Ethernet controller, Wifi, etc. could be found in external chips. Many of those chips were produced and owned by companies other than Intel or AMD. Over time, as more and more functionality could be put into a single chip, many of the afore mentioned functionalities moved into the x86 CPU and the surrounding Intel chipset. In 2010 Intel took a major step and included the graphics processor, the GPU, in their chipset. This pretty much killed the mass market for stand-alone GPUs and since then, Nvidia (GeForce) an AMD (Radeon) GPUs are mostly used in gaming and special application PCs, i.e. in niche markets. Now it looks like Intel has taken the next step and the 2017 evolution of the Core-i processors will now also include the digital part of the Wifi controller.
Continue reading Like the GPU, WiFi Now Moves Into The Intel CPU
Freifunk – Sharing My Internet Connectivity While On Vacation – Part 2
This post continues the tale of my Freifunk experience I had while spending a week on a castle in Germany. In this part I’ll have a closer look at the performance of my network node and how it was used during the time I ran it at the castle.
Continue reading Freifunk – Sharing My Internet Connectivity While On Vacation – Part 2
Freifunk – Sharing My Internet Connectivity While On Vacation – Part 1

I recently went on vacation for a week to a castle in Germany which is a bit off the beaten path. The castle and surroundings are beautiful but I knew from a previous trip that their Wifi Internet connectivity is not available in all rooms. However, I also knew that LTE coverage is quite o.k. in the area so I wasn’t particularly worried about connectivity and instead thought about how I could safely share my Internet connectivity with others while being there.
Continue reading Freifunk – Sharing My Internet Connectivity While On Vacation – Part 1
Instant Printer Detection and Use In Ubuntu 16.04
There have been the days no matter on which operating system when installing the driver for a new printer was a real pain. Linux has been no exception and it was probably the platform on which this procedure was the most painful. After all, especially companies that are on the cheap side of the market often don’t bother to provide printer drivers for Linux so it’s up to the community to do that. I’ve come quite a number of different printers from different manufacturers over the years and I can’t remember a single one that wouldn’t work after a bit of configuration. While the added effort is obviously a disadvantage the big plus is that community drivers prevent closed source software from invading your system and keep bloatware and advertising pop-ups away from your system.
HP is one of the positive and notable exceptions in the Linux world. Their open source driver suite for their printers and scanners works well indeed, comes as a part of many Linux distributions and I had very good experiences with it over the years when I had to connect to HP products. Recently, I noticed that things have advanced a step further (in Ubuntu 16.04 which I am using right now but it is most likely included in other distributions as well) as the HP printer I connected to my notebook over USB was detected automatically and drivers were installed without any user interaction. No model selection, no questions. Perfect!
Using the GSM Timing Advance to Find an LTE Base Station
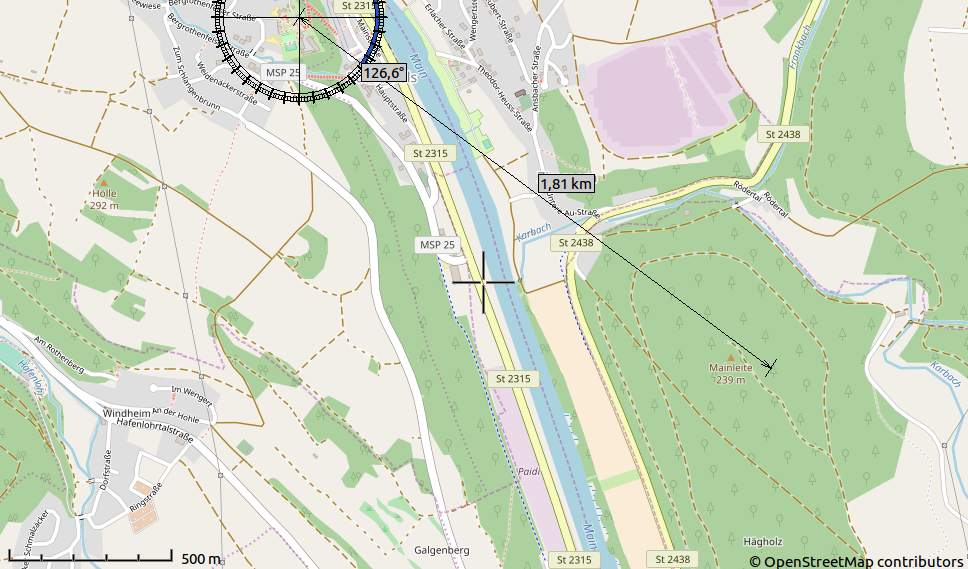 Perhaps some of you still remember the days when GSM base stations were spaced far apart and it was fun to search for them by using the timing advance information shown in the hidden monitoring tool of your GSM phone? Well, perhaps not but this method came in handy again when two people asked me within a few days of each other how they could locate the base station from which their hybrid DSL/LTE home gateway was served so they could perhaps improve their data rate by re-locating their LTE modem.
Perhaps some of you still remember the days when GSM base stations were spaced far apart and it was fun to search for them by using the timing advance information shown in the hidden monitoring tool of your GSM phone? Well, perhaps not but this method came in handy again when two people asked me within a few days of each other how they could locate the base station from which their hybrid DSL/LTE home gateway was served so they could perhaps improve their data rate by re-locating their LTE modem.
Continue reading Using the GSM Timing Advance to Find an LTE Base Station
From Teletype to Touchscreen

So how exactly did we end up with graphical user interfaces, touch screens and shell windows? Apart from improving my understanding of how a CPU really works, understanding the evolution of how users interact with a computer with a keyboard and screen, or a touch sensitive screen on mobile devices, and how this maps into hardware is a favorite past time of mine. So how did we end up with pixels? Continue reading From Teletype to Touchscreen
Book Review – Hackers by Steven Levy
Just shortly before I got my first computer back in the mid-1980s, Steven Levy wrote “Hackers”. The book has become so famous over the years that there’s quite a long entry about it on Wikipedia. I’m not sure why I haven’t picked it up earlier as the story of the book ends just by the time I got started back then and thus would have given me a good idea of why I found things in place as they were.
Recomended Froscon 2017 Talks
 It’s summer time and while most people go on vacation it’s also the time of summer camps and hacker conferences. Last weekend I went to Froscon in Sankt Augustin in Germany for the third time. Close to Cologne and Bonn and not as over-run as Congress in December it’s also a great place to discover new things and get inspired. Back in 2015, for example, I discovered Conversations at the conference, a great XMPP messaging app that I’ve been using ever since. I like to participate rather than to just attend so I was happy to see that the organizers had set up the ‘Angel’-system also used during the CCC congresses for people to sign-up for helping with various tasks during the event. I singed myself up for some video streaming and recording shifts, for looking after hacker kids for a while and also ended up helping to prepare lunch for the team. A nice mix. But besides being part of the conference and talking to people I also went there primarily for the talks. Here are my personal recommendations (most talks are in German, however) from the great choice now online at media.ccc.de:
It’s summer time and while most people go on vacation it’s also the time of summer camps and hacker conferences. Last weekend I went to Froscon in Sankt Augustin in Germany for the third time. Close to Cologne and Bonn and not as over-run as Congress in December it’s also a great place to discover new things and get inspired. Back in 2015, for example, I discovered Conversations at the conference, a great XMPP messaging app that I’ve been using ever since. I like to participate rather than to just attend so I was happy to see that the organizers had set up the ‘Angel’-system also used during the CCC congresses for people to sign-up for helping with various tasks during the event. I singed myself up for some video streaming and recording shifts, for looking after hacker kids for a while and also ended up helping to prepare lunch for the team. A nice mix. But besides being part of the conference and talking to people I also went there primarily for the talks. Here are my personal recommendations (most talks are in German, however) from the great choice now online at media.ccc.de:
1 TB SSDs the same price as 3 Years Ago
Slowly but steadily the SSDs in the notebooks in the family keep filling up so at some point in the not too distant future I either migrate from 1 TB to 2 TB SSDs or have to think about strategies to put some of the files to offline/home storage. While I would obviously prefer the first option the reality is that SSD prices haven’t dropped much over the past 3 years. Where’s Moore’s law? Continue reading 1 TB SSDs the same price as 3 Years Ago