Last year I wrote about a 5G Americas whitepaper that describes how 3GPP has standardized the 5G core in a way that lends itself for cloud based implementation. In short, that means that control plane functions are split into microservices, deployed on bare metal clusters in containers and managed with Kubernetes. So far the theory. Now, products designed this way are announced by first telecommunication vendors.
Continue reading The Cloud Based 5GC – From Theory To PracticeKubernetes Intro – Part 4 – Persistent Storage
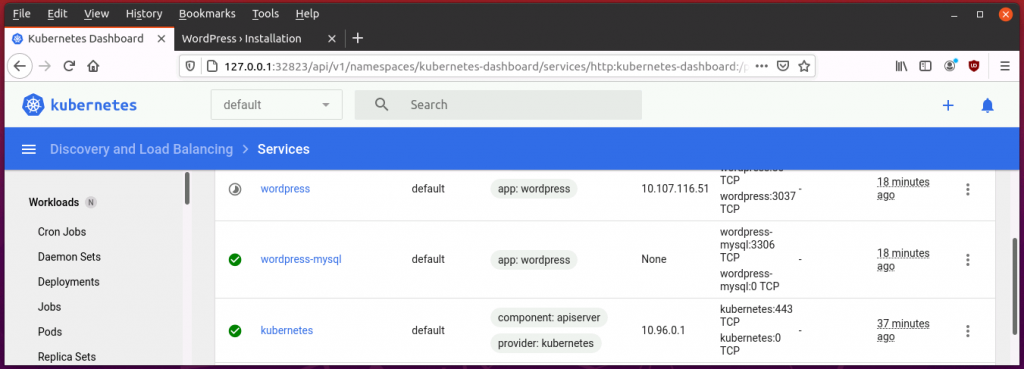
I’m almost happy with the basic hands-on understanding I have gained about Kubernetes about which I have written in part 1 to 3 of this series. I understand much better now how Kubernetes manages Docker containers, how it abstracts and manages the distribution of containers in a cluster of servers and how it makes services running in containers reachable from the outside world. From a developer and network administrator point of view, however, one important thing is still missing: How does Kubernetes manage persistent storage for containers? So let’s have a look at this and also experiment with a hands-on example: Running a WordPress Blog with a MySQL database in a Kubernetes cluster. As you will see, it’s not rocket science.
Continue reading Kubernetes Intro – Part 4 – Persistent StorageKubernetes Intro – Part 3 – Create, Dockerize and Push Into the Cluster
So here’s the story so far: In parts 1 and 2 of my Kubernetes intro story, we have set up a Minikube Kubernetes Cluster. We then deployed a container with an app inside, which was downloaded directly from the Kubernetes image hub, into our cluster. Our cluster is small, it only contains one worker node and the container we put into a pod was the only service running in our cluster. If you could follow this description you are now ready for part 3 of the story. Based on what we have done so far we now create our own app, create a Docker image in which the app can run and then deploy it into our Kubernetes cluster. In the end we will have two services running in the cluster: The Echoserver app from part 2 and the app we are going to put together in this episode.
Continue reading Kubernetes Intro – Part 3 – Create, Dockerize and Push Into the ClusterKubernetes Intro – Part 2 – The Dashboard
In part 1, I’ve given an introduction to my path to learn more about Kubernetes with a hands-on approach. The story ended with Minikube being installed and a first sample application (the ‘http echosever’) up and running in a container that is managed by Kubernetes. With all of this in place now, the next logical step is to have a closer look at the browser based Kubernetes dashboard and what it shows about this small container deployment.
Continue reading Kubernetes Intro – Part 2 – The DashboardKubernetes Intro – Part 1

When we are talking about the 5G Core and implementations based on containers the story does not end with Docker containers. As a 5GC is not only based on one server and needs lots of redundancy, a management (orchestration) tool is required to manage containers across a large number of servers. There are several tools for this but it seems that Kubernetes is the tool of choice for most these days. I did a lot of reading about Kubernetes but the whole thing was still too abstract for me no matter how much I read about it. So I decided to get some hands-on experience myself. Here’s how I went about it in case you’d like to give it a go as well.
Continue reading Kubernetes Intro – Part 1Dockerize Me – Containers Managing Containers – Part 5
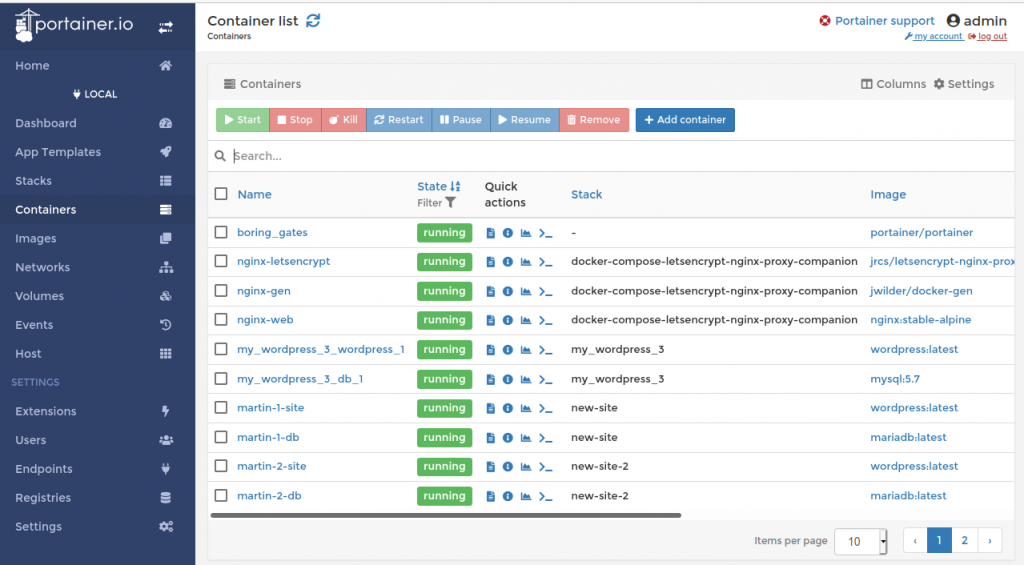
In the previous episode, I’ve moved a WordPress Blog from the simple installation of part 1 to the more sophisticated reverse proxy setup I have put together in part 3 to demonstrate that containers are ‘portable’ between different servers with little effort. Moving the container also showed that the nginx-gen container recognizes when new containers are started and can actually access the environment of that container. It uses this information in turn to create a vhost configuration for the reverse proxy and triggers the creation of a new Letsencrypt certificate. The big question: How does the software that runs in the nginx-gen container get informed that a new container has started and how and why can it access the environment variables of another container? After all, while this is a nice functionality it also raises the question of container security and privacy. Can any container look at the inside of other containers on a server?
Continue reading Dockerize Me – Containers Managing Containers – Part 5Dockerize Me – Moving Containers To Another Host – Part 4
In part 3 of this series we’ve created a reverse proxy setup with Docker containers in the public cloud to serve the content of several web services from independent docker containers with individual domain names. In this episode I’ll test the concept that containerized applications can easily be moved from one host to another.
Continue reading Dockerize Me – Moving Containers To Another Host – Part 4Dockerize Me – Several Services and LetsEncrypt – Part 3
After the basic installation of Docker and getting a WordPress blog up and running in Docker containers in part 1, this part of my Docker series will take a look at how to add two important features to the setup:
- TLS certificates and LetsEncrypt with auto-renewal
- How to host several websites on one server that are accessible on the same ports (80 for http and 443 for https)
Dockerize Me – Cheat Sheet and Pyramid of Trust – Part 2
In part one of my ‘Dockerize Me’ story, I’ve been describing the reasons why I want to learn more about Docker and gave some first tips and tricks how to quickly install it with a few commands on a Debian based server. A first docker-compose project then demonstrated how to quickly spin-up a WordPress container that talks to a database in another container that stores the website’s configuration, the text of the blog articles, comments, etc. Before expanding on this example in part 3, here’s a cheat sheet of Docker and docker-compose commands that I use frequently. Also, I think it’s a good thing at this point to spend some thoughts on the pyramid of trust when getting images from Docker Hub.
Continue reading Dockerize Me – Cheat Sheet and Pyramid of Trust – Part 2Dockerize Me – My Personal Docker Bootstrap Voyage – Part 1

Over the years I’ve been looking at Docker every now and then. That’s because for one thing I am interested in the concept of deploying software in lightweight containers instead of VMs and also because I am running two pieces of software in Docker containers on my servers as well. But that was it until now because Docker has a steep learning curve and it was pretty pointless for me to really go for it unless I have a use case myself. This year, however, my interest started growing for a number of reasons, so I decided to ride the wave and put together a curriculum that fits my needs. So here’s what motivated me to spend the time and effort and my recommendations for how to go about it.
Continue reading Dockerize Me – My Personal Docker Bootstrap Voyage – Part 1