Before the recent Twitter implosion, Mastodon was a nice place. I typically followed others that had interesting things to share, which means, to me, ideas and projects that would better me professionally or personally. It was a joy to browse through my timeline in the morning and there was hardly a day when I didn’t pick up an interesting idea. But then Twitter imploded and Mastodon saw a massive influx of new people. This totally changed the equation for me.
Continue reading Creating My Own Filter Bubble In MastodonReality Bites, Part 6: The G3000 Avionics on Steroids in That Simulator

In the previous post back in January on my flight simulator adventures, I’ve described my step from a small propeller plane to the somewhat more powerful turbocharged Daher TBM 930. While that doesn’t give a lot of benefits from a Visual Flight Rules (VFR) perspective, having a faster plane for Instrument Flight Rules (IFR) flying is a great thing, as it offers additional range and hence, more controlled airports to fly into. This is particularly helpful when flying in the Vatsim environment, where ‘real virtual’ air traffic controllers keep you save in the sky, but only cover select larger airports. The catch so far: The Garmin G3000 flight management system (FMS) has lacked a number of important features so far, which made IFR flying quite a bit more challenging, particularly in high workload situations. So I was really delighted that in the update in January 2003, the G3000 avionics got a major overhaul. Let’s have a look at that.
Continue reading Reality Bites, Part 6: The G3000 Avionics on Steroids in That SimulatorPrice Development of My Used Z440 Workstation

About two years ago, I bought a 5 year old used HP Z440 workstation with a 6 core Xeon E5-1650 v4, 32 GB of RAM and an Nvidia M2000 graphics card for around 800 euros. At the time I wanted to have some CPU processing power with little noise and an Nvidia graphics card that could do H.264 video encoding and decoding in hardware. This turned out to be a great investment, as I use the workstation daily to run a number of computing intensive virtual machines and also make good use of the hardware video encoder, all with pretty much zero noise emission from below the desk. By now, the hardware is about 7 years old and one would think that even refurbishers would be out of stock by now and sell the system at a significantly lower price. Turns out that this is not the case.
Continue reading Price Development of My Used Z440 Workstation5G n78 Shines in the Austrian Alps
Recently, I’ve been on a two week skiing trip in Bad Gastein, a small village in the Austrian alps. As usual and also because my default cellular connectivity did not meet my needs, I had a closer look at the local connectivity options and gained some interesting insights.
For testing purposes and of course for redundancy, I have subscriptions of two premium mobile network operators in Germany, and both usually also provide excellent service while roaming. During the day, LTE data rates in the automatically selected roaming network were well beyond 100 Mbps in the downlink and well over 80 Mbps in the uplink. 5G was not yet available on the local cell tower, but at those data rates, I didn’t really mind. In the evenings, however, the automatically selected network got more and more loaded, and by 8 pm, downlink speeds consistently slowed to 1-2 Mbps. Also, round trip times increased from 100 ms to well over 200 ms. In the uplink direction, however, I still got 50 Mbps. A clear sign of congestion and totally unusable for many things.
Continue reading 5G n78 Shines in the Austrian AlpsWhen All Else Fails – The Garmin InReach Mini 2 – Part 11 – More About Power Consumption
In part 6, I’ve taken a look at how much power my Garmin InReach draws in various scenarios. Depending on where the device was located and used throughout the days, the battery would last me anywhere between 16 days in the best case and only a single day in case no satellite can be reached all day long. On a recent skiing trip , I now had a look how long the battery would last it tracking, i.e. location recording was enabled in addition to sending and receiving the occasional message over the Iridium network.
Continue reading When All Else Fails – The Garmin InReach Mini 2 – Part 11 – More About Power ConsumptionWhen All Else Fails – The Garmin InReach Mini 2 – Part 10 – Some More Notes

The Garmin InReach Mini 2 keeps fascinating me beyond the 9 blog entries I made last year, so needless to say, I took it with me to a recent vacation in the Austrian alps. While experimenting, I had two interesting insights that I thought I should document here: Message time context and where around the globe SOS emergency messages are being sent.
One thing I kept asking myself was if the time shown next to an incoming text message is actually the time the message was received or if it was the time it was sent. On mobile phones that use a cellular or Wifi network, these are usually the same. Over satellite, however, there can be a significant delay delivering the message for two reasons:
Continue reading When All Else Fails – The Garmin InReach Mini 2 – Part 10 – Some More NotesNTN Part 1 – 3GPP Rel. 17 – Non-Terrestrial Networks
In recent months, satellite services for smartphones have been hyped a lot. While surprising for many, including me, this didn’t come out of nowhere, and a lot of companies have worked on this topic for quite some time. 3GPP has also picked up the topic a few years ago with study items in 3GPP Release 15 and 16. Now, with Release 17, the LTE and 5G NR air interfaces have been extended for use over satellites. The term for this in 3GPP: Non-Terrestrial Networks (NTN). So let’s have a look at what has actually been specified:
Continue reading NTN Part 1 – 3GPP Rel. 17 – Non-Terrestrial NetworksLenovo Thinkpad BIOS Update Games
Over the past years, a lot has happened to ensure that the BIOS firmware of notebooks, workstations and servers can be updated without great fuzz. An automatic downloader and installer is now part of the update procedure of ‘that default operating system’ used by most people. On the Linux side, many companies these days upload their BIOS update files to fwupd.org, which is used as a repository by the firmware update client of major Linux distributions.
So far, so good… However, even though the number of manufacturers supplying images to fwupd.org is rising, there is still room for improvement, and it seems that manufacturers have different amounts of ‘Linux love’ depending on the device series. Let’s take the Lenovo Thinkpad line as an example and the devices I have at home. Sadly, depending on whether a notebook is from the X-,T-,L- or E-series, Linux firmware update support ranges from excellent to, well, let’s say rudimentary, even for the latest and greatest devices.
Continue reading Lenovo Thinkpad BIOS Update GamesNVMe SSD Password Puzzle
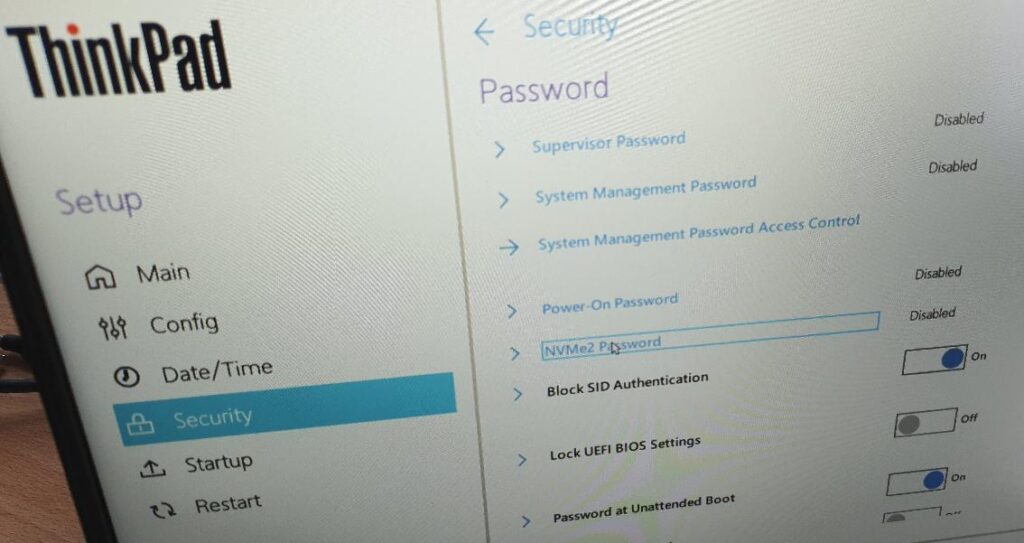
When SATA SSDs where still in fashion a few years ago, a power-on drive password could be set in BIOS, which was then stored on the drive. While this didn’t encrypt the data, and every notebook manufacturer had its own way to translate what was typed-in to what was stored on the drive, it was a common function. As the world moved on to NVMe M.2 SSDs in notebook, it looks like this has become an optional function. While I could activate the password on my somewhat more expensive Samsung SSDs, the option disappears from the BIOS setup screen when I put-in an SSD of another manufacturer. But it looks like the story is more complicated.
Continue reading NVMe SSD Password PuzzleNextcloud – Upgrading to Ubuntu 22.04
I’m running four Nextcloud instances, all of them in separate virtual machines on Ubuntu 20.04. The problem: Ubuntu 20.04, despite still being rather young, comes with PHP 7.4, which has been declared end of live recently, and Nextcloud has announced that they will no longer support this PHP version in their next release. So while I would probably still have a year or so to do something about this, I’ve decided to be proactive and do a release upgrade of the operating system to Ubuntu 22.04, which includes the latest and greatest PHP version (8.1) at the time of writing. As expected, there were a few bumps along the way and the Apache web server installation on all instances needed some manual tweaking after the OS upgrade. The interesting touch: Even though the virtual machine images were very similar, each Apache installation required a different nudge.
Continue reading Nextcloud – Upgrading to Ubuntu 22.04